[TryHackMe] Disk Analysis & Autopsy
A walkthrough for the Disk Analysis & Autopsy room, available on the TryHackMe platform.
![[TryHackMe] Disk Analysis & Autopsy](/content/images/size/w2000/2021/06/forest-931706_1920.jpg)
Difficulty level: Easy/Medium
Aim: Use Autopsy to investigate artifacts from a disk image.
Link: https://www.tryhackme.com/room/autopsy2ze0
Introduction
The official page describes Autopsy as: "the premier open source forensics platform which is fast, easy-to-use, and capable of analyzing all types of mobile devices and digital media. Its plug-in architecture enables extensibility from community-developed or custom-built modules. Autopsy evolves to meet the needs of hundreds of thousands of professionals in law enforcement, national security, litigation support, and corporate investigation."
The virtual machine within this room contains an Autopsy case file and the corresponding disk image. Ingest modules have already been run.
I will assume you have already deployed this VM, connected via RDP, opened the Autopsy case file and repointed Autopsy to the disk image file.
Walkthrough
Let's get started!
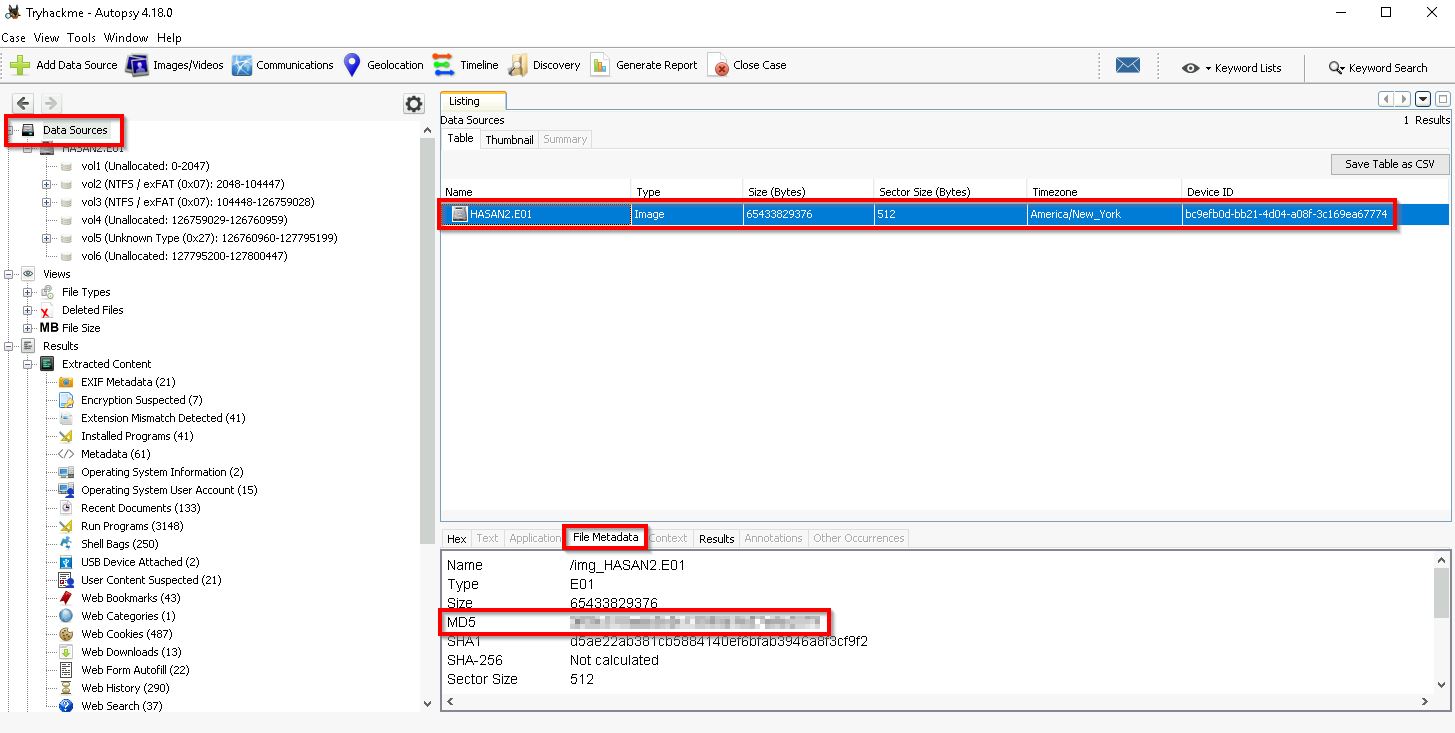
Q1. What is the MD5 hash of the E01 image?
This can be obtained by looking at the metadata of the disk image:
Data Sources > HASAN2.E01 > File Metadata
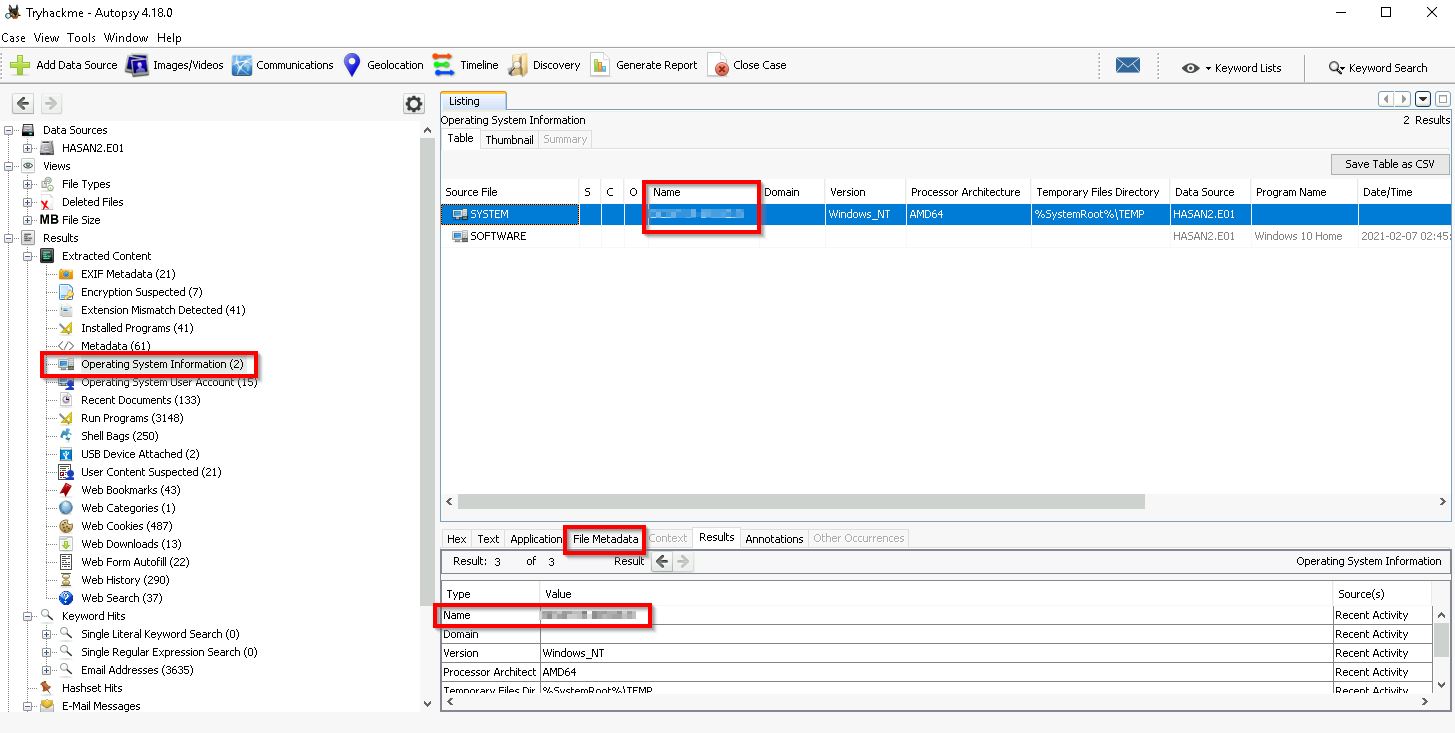
Q2. What is the computer account name?
This can be found in the section for Operating System Information:
Operating System Information > SYSTEM > File Metadata
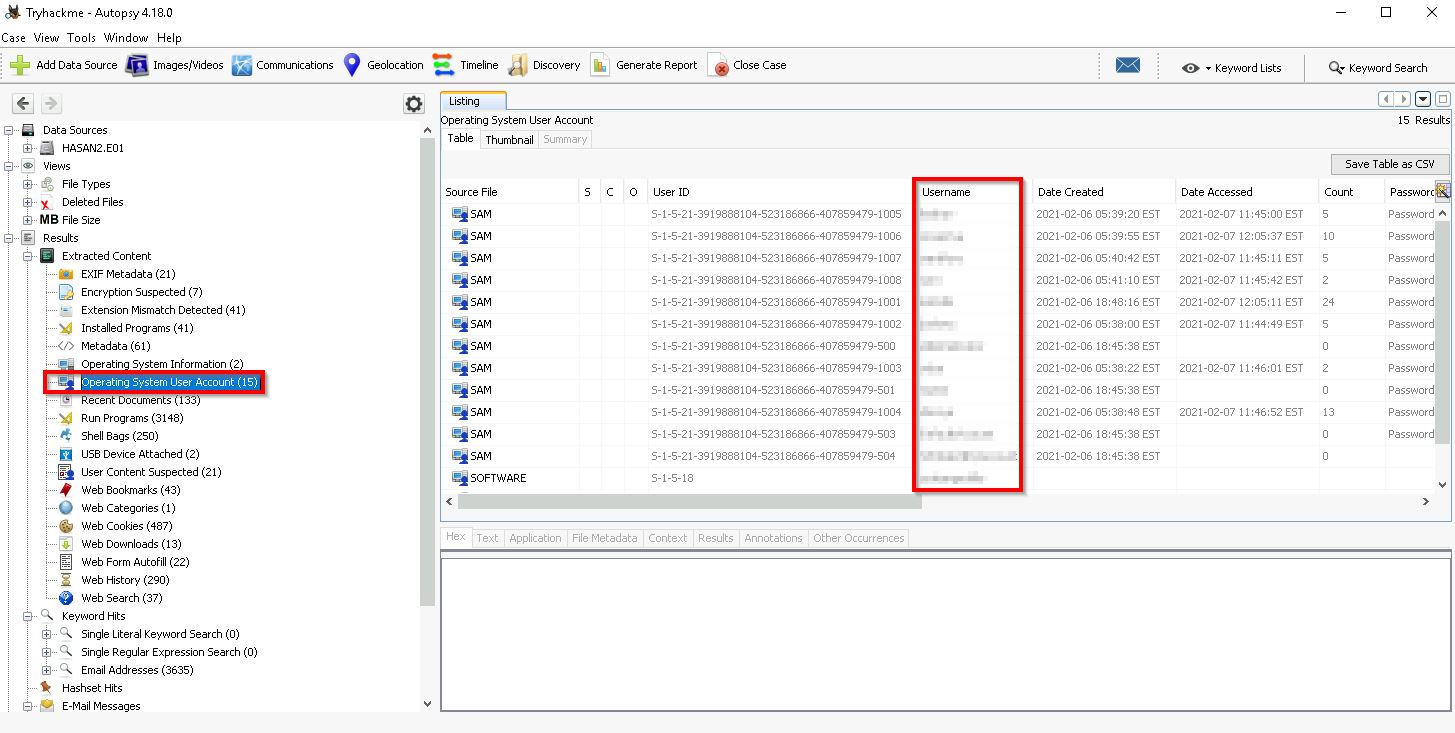
Q3. List all the user accounts (in alphabetical order)
Details can be found in the Operating System User Account section:
Operating System User Accounts > Username column
Q4. Who was the last user to log into the computer?
Check the 'Date Accessed' column within the Operating System User Account section.
Q5. What was the IP address of the computer?
To obtain this information we need to look at the contents of the following file:
Data Sources > HASAN2.E01 > Vol3 > Program Files (x86) > Look@LAN > irunin.ini
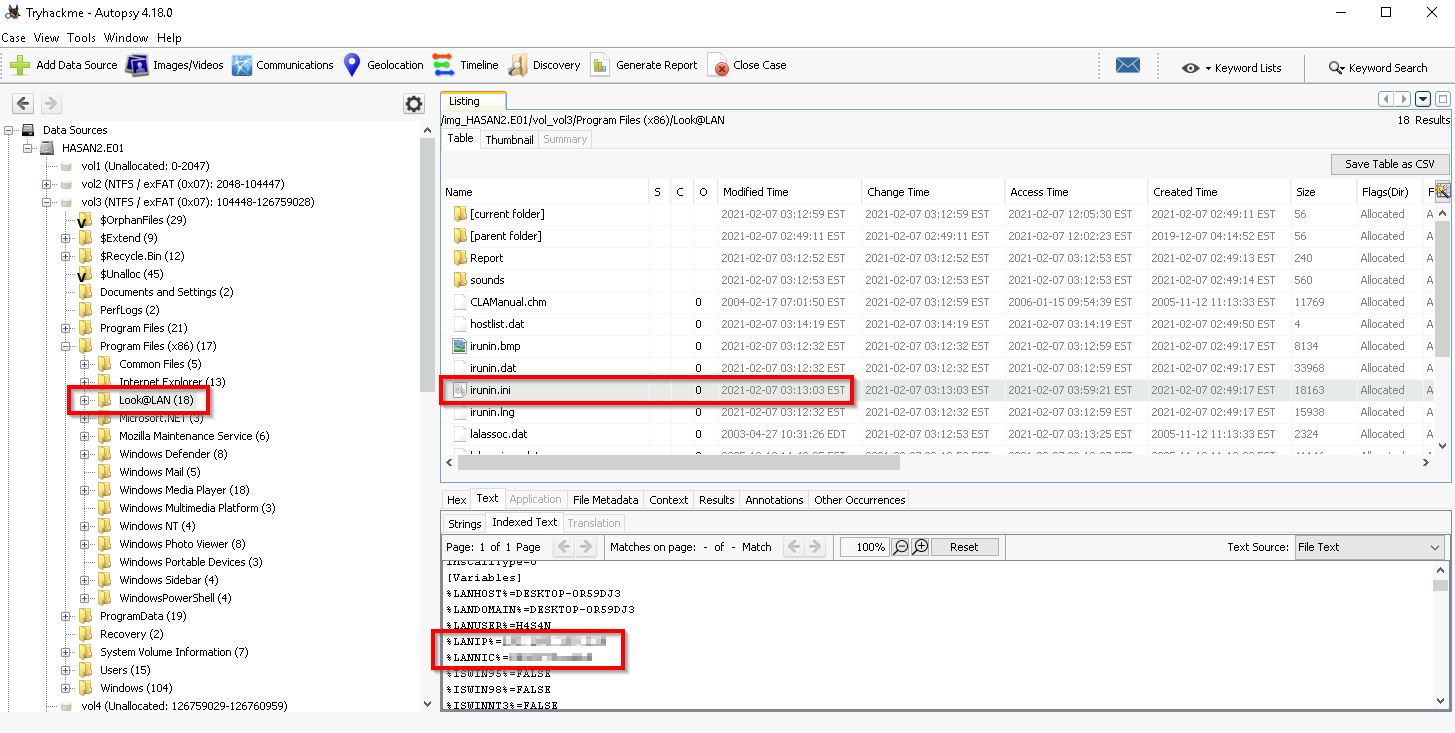
Q6. What was the MAC address of the computer? (XX-XX-XX-XX-XX-XX)
This can also be found in the irunin.ini file as above - see %LANNIC%
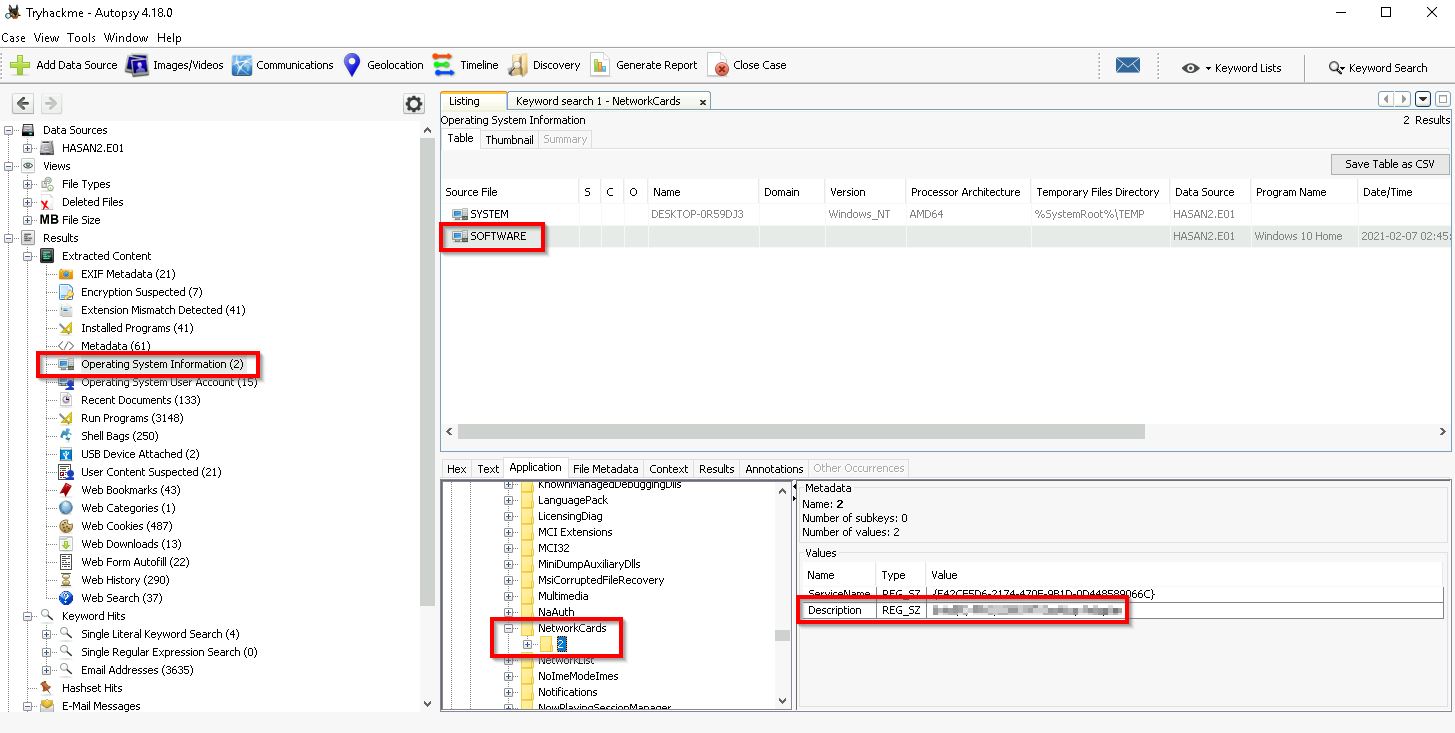
Q7. Name the network cards on this computer.
For this information we need to head back to the Operating System Information section, select SOFTWARE and then browse to the following path:
ROOT/Microsoft/Windows NT/CurrentVersion/NetworkCards/2
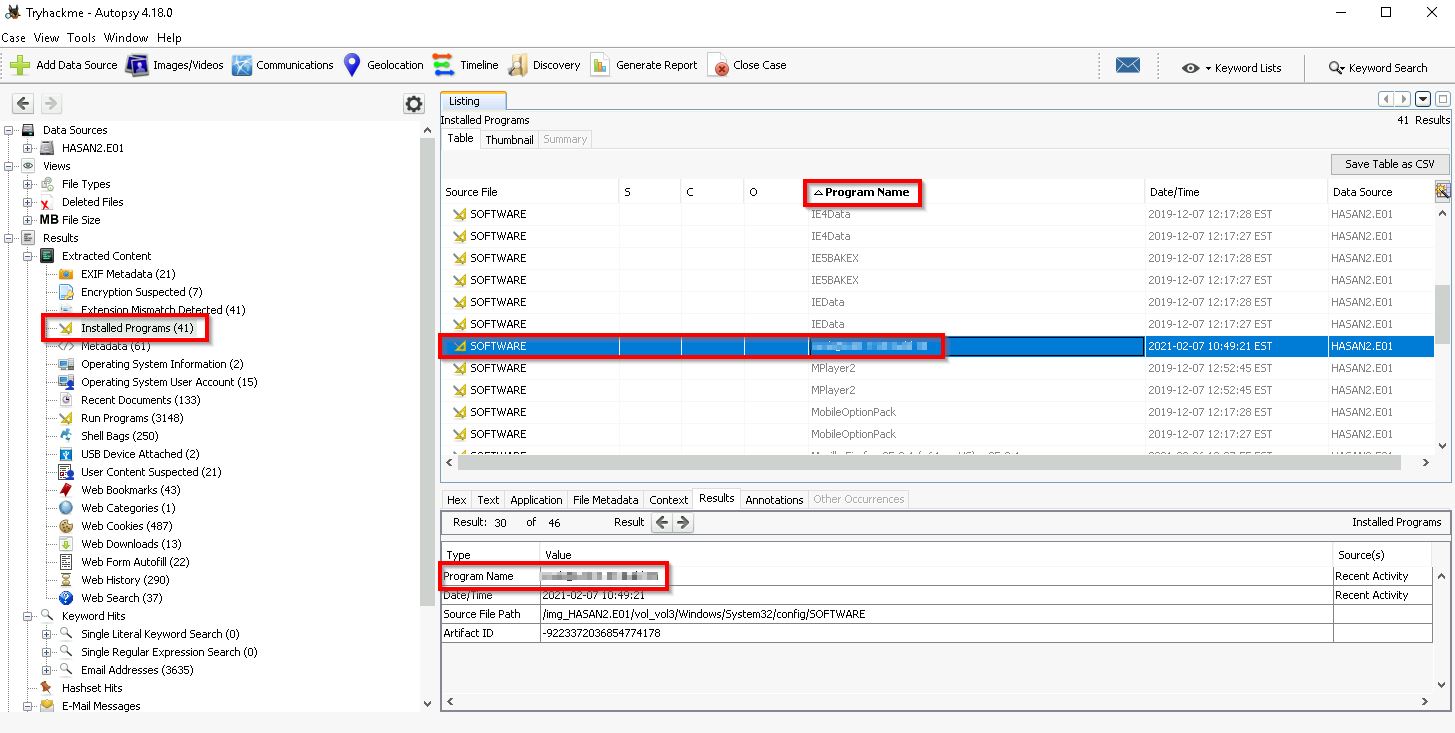
Q8. What is the name of the network monitoring tool?
To answer this, take a look at the Installed Programs section and look for network-related programs (it might help to sort the Program Name column in ascending order):
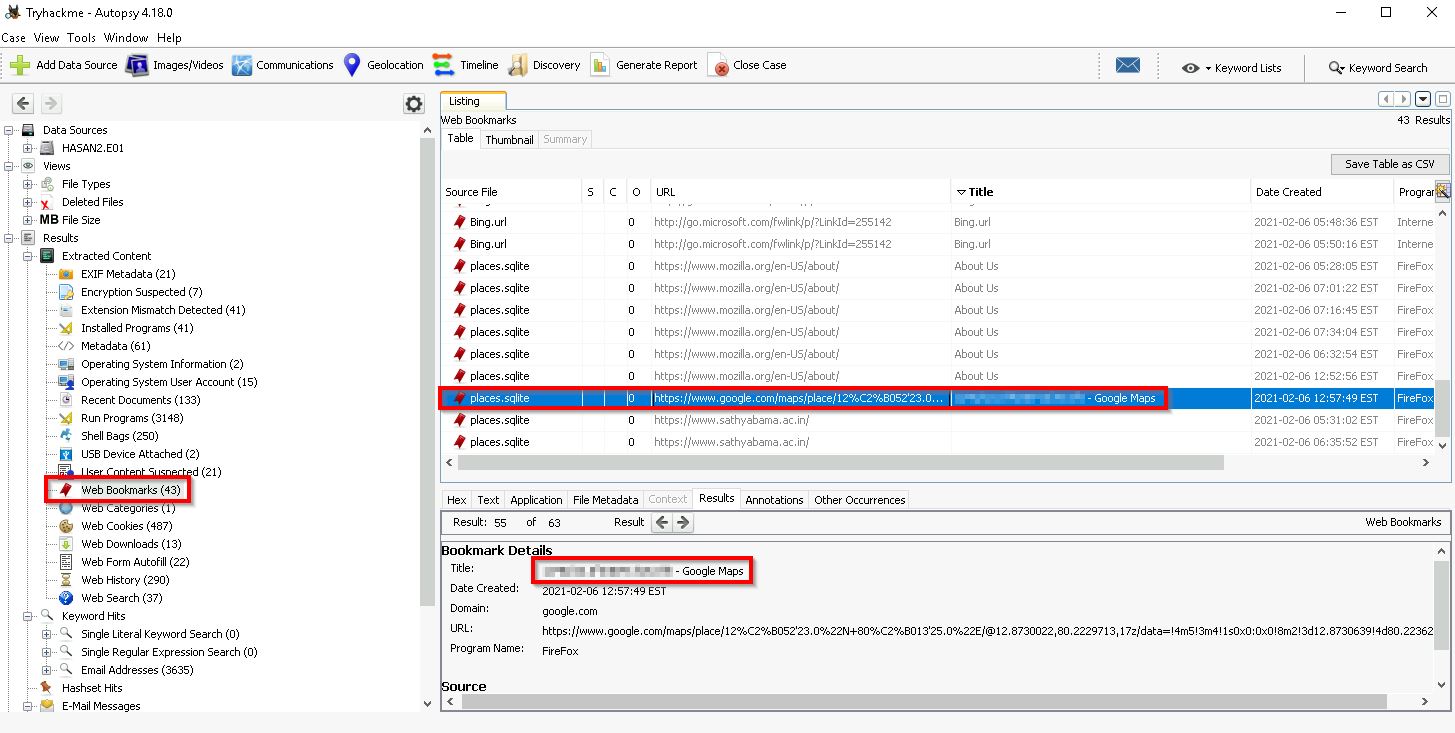
Q9. A user bookmarked a Google Maps location. What are the coordinates of the location?
Head over to the Web Bookmarks section to find the answer for this one:
Q10. A user has his full name printed on his desktop wallpaper. What is the user's full name?
Images/Video is the place to look. Specifically, the folders for each User:
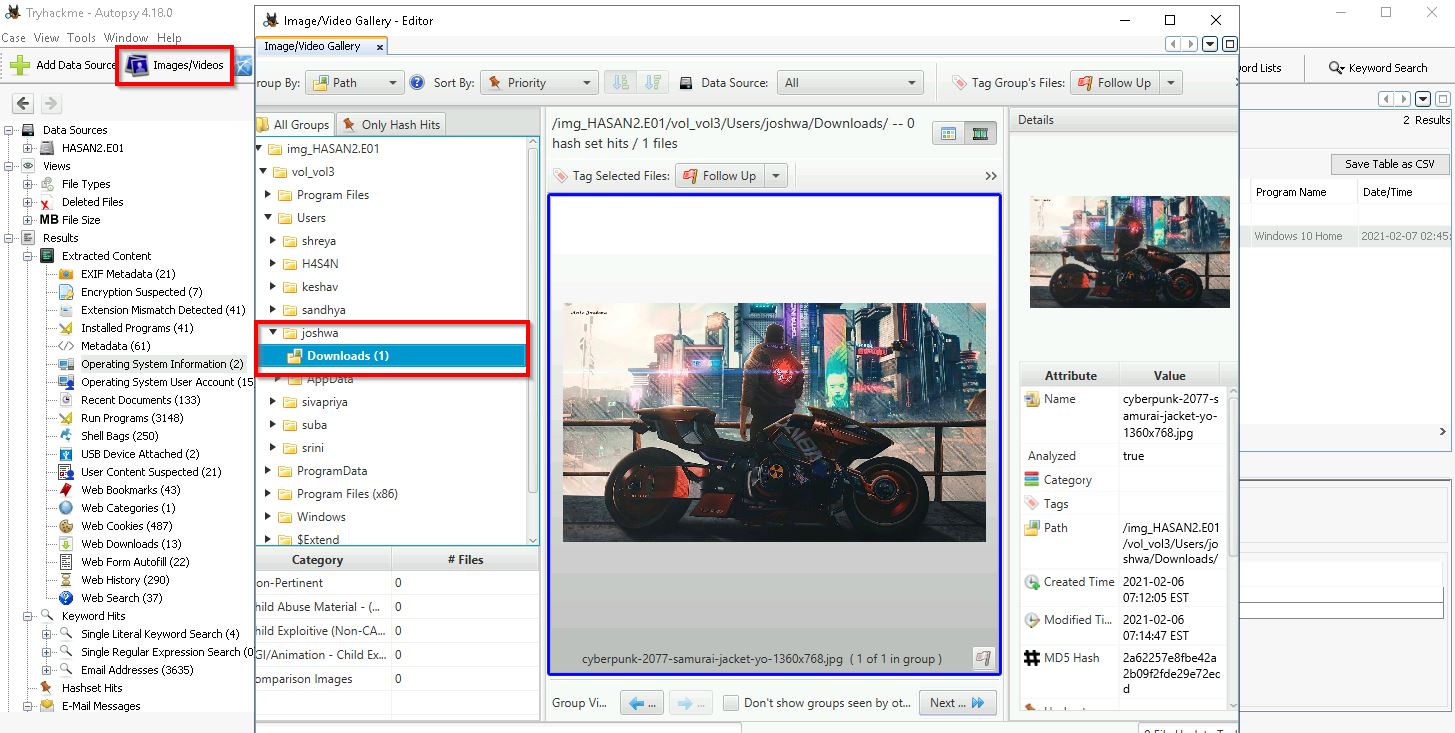
The wallpaper file can be exported from Autopsy by right-clicking the image and selecting "Export".
Once exported, this can be found in the "\Case Files\Export" folder on the Desktop of the Autopsy VM. Take a look at this file to get the answer.
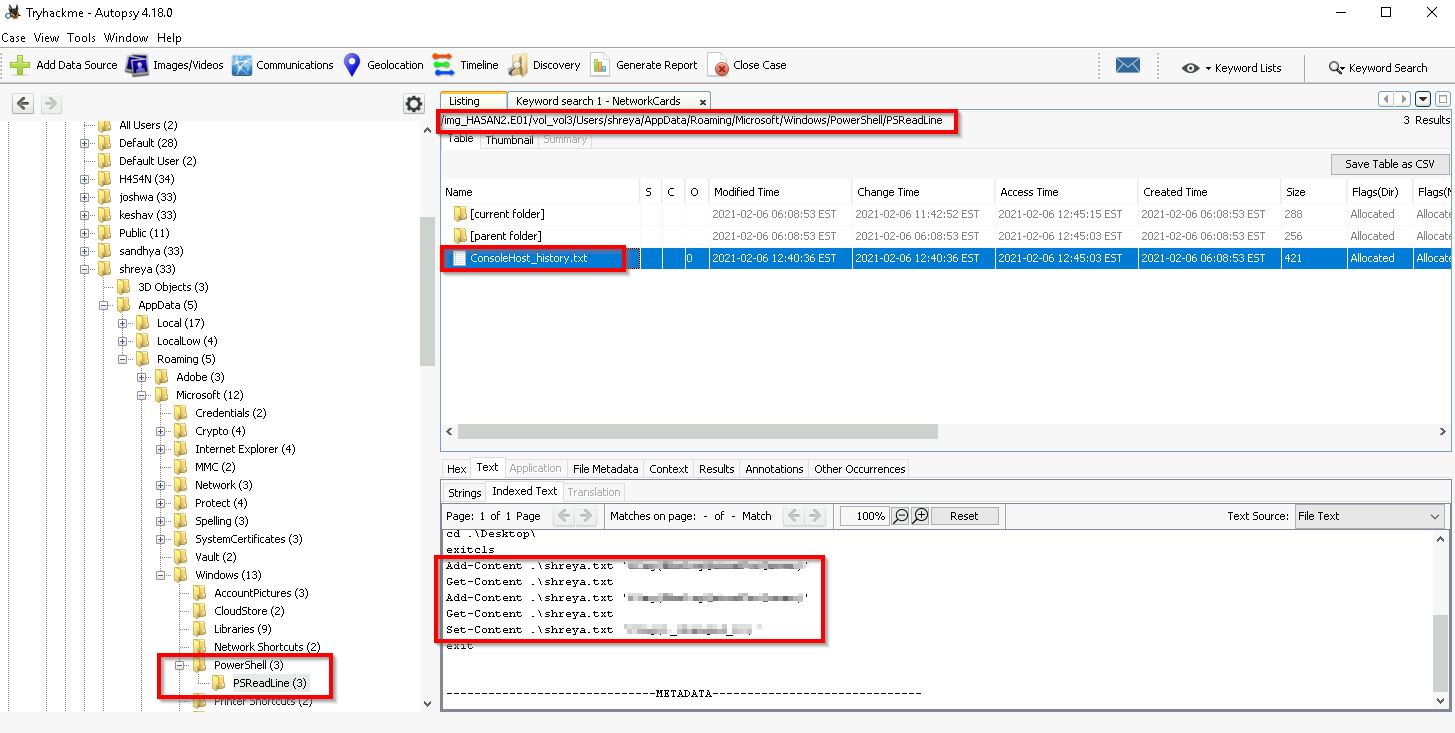
Q11. A user had a file on her desktop. It had a flag but she changed the flag using PowerShell. What was the first flag?
My process to find this answer was to check the PowerShell history file for each user located at the following path:
Data Sources > HASAN2.E01 > Vol3 > Users > 'username' > AppData > Roaming > Microsoft > Windows > PowerShell > PSReadLine > ConsoleHost_history.txt
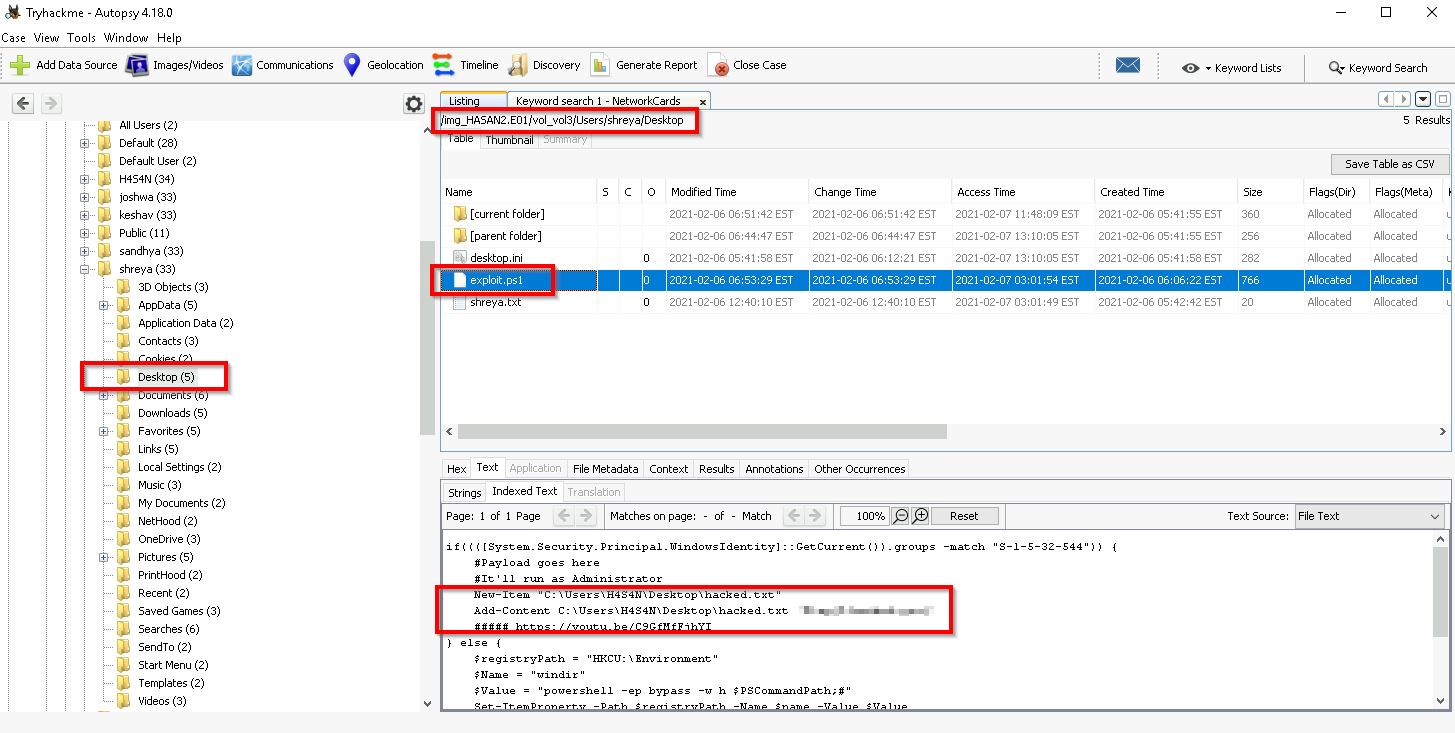
Q12. The same user found an exploit to escalate privileges on the computer. What was the message to the device owner?
Checking this users Desktop we find a file named 'exploit.ps1' which will give us the answer we need:
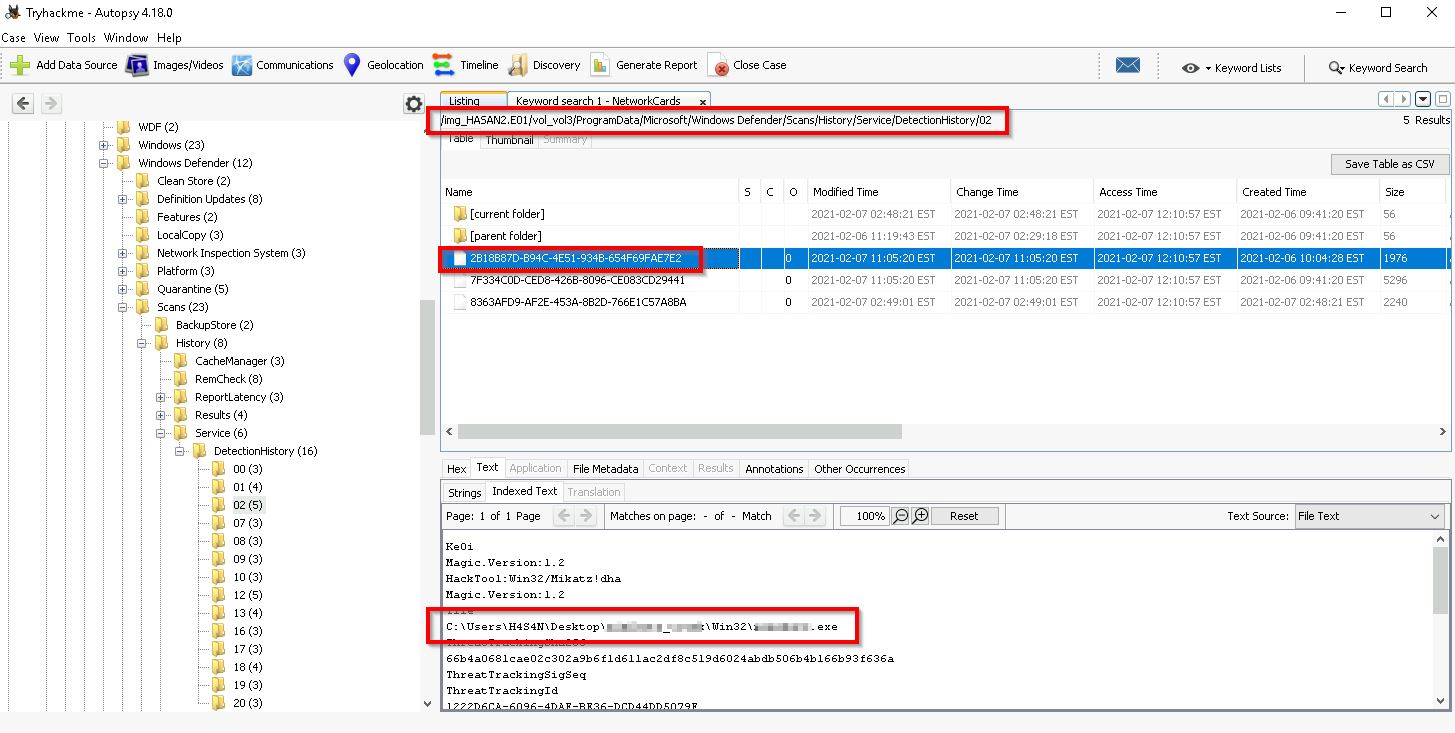
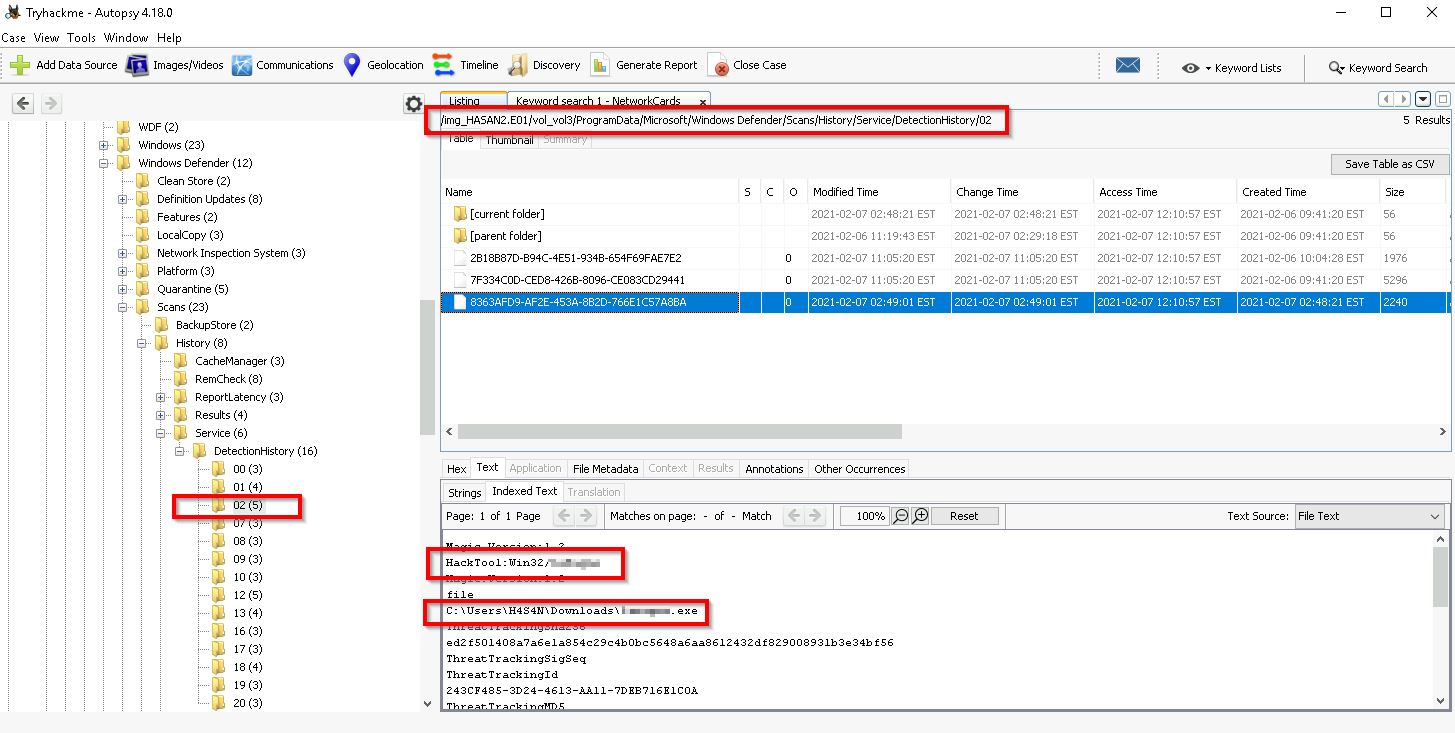
Q13. Two hack tools focused on passwords were found in the system. What are the names of these tools? (alphabetical order)
With these being hack tools, there is a good chance that Windows Defender might have detected these. We can look at the Windows Defender history here:
Data Sources > HASAN2.E01 > Vol3 > Program Data > Microsoft > Windows Defender > Scans > History > Service > DetectionHistory > 02
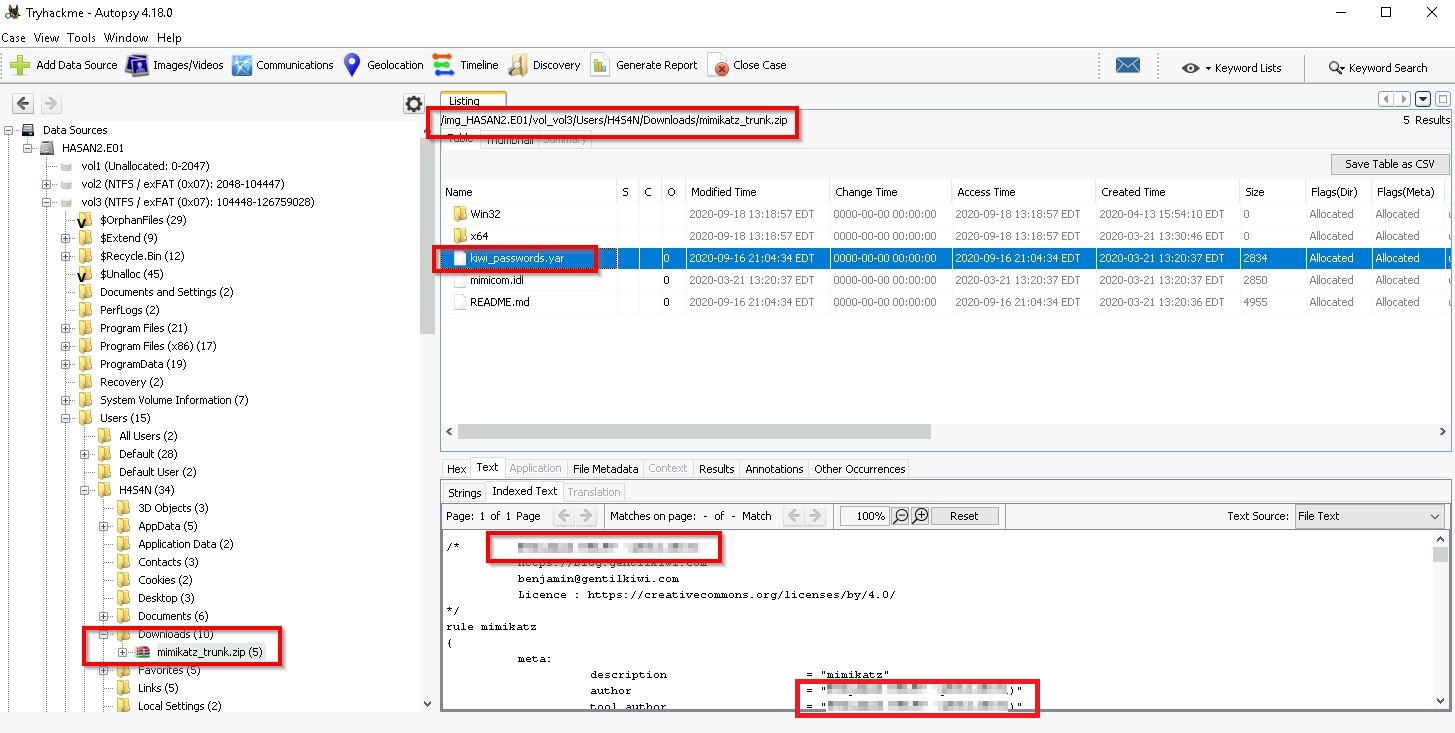
Q14. There is a YARA file on the computer. Inspect the file. What is the name of the author?
This one took me a bit longer to find than I expected! The answer lies within a file with the .yar extension, which can be found within an archive located in the Downloads folder of a particular user:
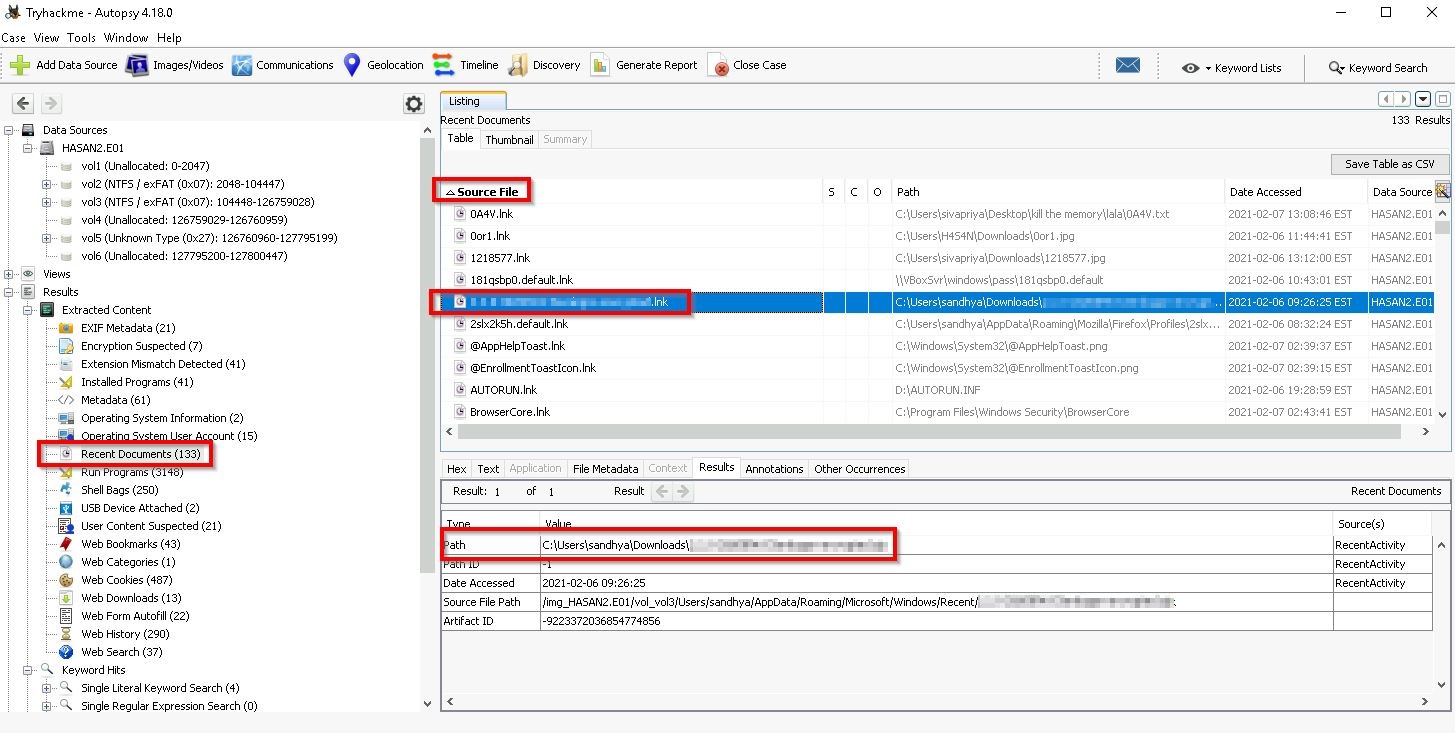
Q15. One of the users wanted to exploit a domain controller with an MS-NRPC based exploit. What is the filename of the archive that you found? (include the spaces in your answer)
For the final question, take a look in the Recent Documents section and sort the Source column to identify the archive (the exploit name should scream out to you!)
That's all there is to it! :)
Please feel free to contact me via Twitter and thanks for reading.

